Abstract
The twin-field class quantum key distribution (TF-class QKD) has experimentally demonstrated the ability to surpass the fundamental rate-distance limit without requiring a quantum repeater, as a revolutional milestone. In TF-class QKD implementation, an optical phase-locked loop (OPLL) structure is commonly employed to generate a reference light with correlated phase, ensuring coherence of optical fields between Alice and Bob. In this configuration, the reference light, typically located in the untrusted station Charlie, solely provides wavelength reference for OPLL and does not participate in quantum-state encoding. However, the reference light may open a door for Eve to enter the source stations that are supposed to be well protected. Here, by identifying vulnerabilities of an acousto-optic modulator (AOM) in the OPLL scheme, we propose and demonstrate a wavelength-switching attack on a TF-class QKD system. This attack involves Eve deliberately manipulating the wavelength of the reference light to increase mean photon number of prepared quantum states, while maintaining stable interference between Alice and Bob as required by TF-class QKD protocols. The maximum observed increase in mean photon number is 8.7%, which has been theoretically proven to compromise the security of a TF-class QKD system. Moreover, we have shown that with well calibration of the modulators, the attack can be eliminated. Through this study, we highlight the importance of system calibration in the practical security in TF-class QKD implementation.
Similar content being viewed by others
Introduction
Quantum key distribution (QKD), based on the principles of quantum physics, enables two remote parties to securely share a secret key over a public and insecure channel, demonstrating information-theoretic security irrespective of an eavesdropper’s computational power1. Over the past approximately four decades, QKD technology has progressively evolved and matured to such an extent that its practical deployment in optical-fiber networks is now feasible2. Throughout this advancement, the primary objectives have been to achieve extended transmission distances and higher key rates while ensuring robust security performance. However, accomplishing each of these aforementioned objectives presents significant challenges.
Channel loss is a crucial barrier of enhancing the key rate and transmission distance of QKD systems. This is primarily due to the vulnerability of single photons, which are used for encoding quantum keys, to scattering and absorption within the transmission channel. However, amplification of these photons is not feasible3, resulting in reduced detection probabilities over extended distances. In QKD systems without incorporating quantum repeaters, there exists a fundamental limit on the secure key rate known as the Pirandola-Laurenza-Ottaviani-Bianchi (PLOB) bound4. This bound scales linearly with channel transmittance η, denoted as O(η)5.
Fortunately, a recent protocol called twin-field QKD (TF QKD) has been proposed, surpassing the fundamental rate-distance limit and revolutionizing the scalability of both key rate and channel loss to be \(O(\sqrt{\eta })\)6. TF QKD leverages the advantage that two distant peers, Alice and Bob, transmit two optical fields with correlated phase to conduct single-photon interference at an intermediate station named Charlie. This implies that only one photon from either Alice or Bob needs to arrive and be detected at Charlie in order to generate a secret key, while the other peer transmits vacuum states that are inherently immune to channel loss. In addition to overcoming transmission limits, TF QKD also inherits the advantages of measurement-device-independent (MDI) QKD7,8, where Charlie can be fully untrusted as an intermediate station. The security of TF QKD against general attacks has been theoretically proven, establishing a solid foundation for its implementation9,10,11,12,13,14. Following this theoretical development, experimental demonstrations have shown that TF-class QKD outperforms the PLOB bound15,16,17,18,19,20,21,22,23, achieving record-breaking distances up to 1002 km23,24. These achievements highlight the feasibility of implementing intercity QKD without relying on trusted relays.
However, the practical security performance, another crucial aspect of QKD, has not yet been investigated in the context of this novel TF-class QKD. Regarding its implementation, it is quite challenging to generate identical optical fields with correlated phase by two separate parties as required by the protocol. This unique requirement introduces a distinct implementation scheme that may also introduce unforeseen security vulnerabilities. In initial proof-of-principle experiments6,25, the light source was placed at an untrusted location and transmitted to Alice and Bob. Unfortunately, this approach is evidently insecure since Eve can manipulate the quantum signal encoding key information by controlling the light source. To mitigate this vulnerability and strictly adhere to the structure of TF QKD protocol, subsequent experiments equipped each Alice and Bob with separate lasers. However, this mitigation strategy gives rise to a new challenge - ensuring that Alice’s and Bob’s lasers produce optical fields with identical phase correlation. To address this concern, achieving wavelength consistency of the two separate laser sources is accomplished through the laser injection technique. In this technique, Charlie applies a seed laser to independently inject into Alice’s and Bob’s laser sources20,26. However, this scheme potentially introduces a vulnerability for Eve to gain access to the assumed-to-be-protected source station27,28 - Eve could manipulate the seed light via Charlie or exploit the public channel for similar laser-seeding attacks29,30,31. Moreover, TF QKD schemes might also be susceptible to Trojan-horse attacks and induced-photorefractive attacks32,33. Therefore, ensuring practical security in TF-class QKD systems is more intricate compared to previous QKD implementations due to their unique realization schemes and techniques that require heightened attention.
In addition to the aforementioned known threats on these schemes, an advanced technique known as optical phase-locked loop (OPLL) has been extensively employed in recent implementations to achieve persistent stable interference by generating identical optical fields between Alice and Bob15,16,17,19,20,21,22,23,34,35. In this approach, Alice’s and Bob’s lasers are synchronized with a reference laser source for both frequency and phase20,21,22,23. While this method enhances the stability of correlated phases in two optical fields and supports the realization of a secure interference TF-class QKD implementation, its practical security aspects remain unexplored.
In this study, our focus lies on the practical security performance of a TF QKD system employing the OPLL scheme. In this scheme, although the reference light is not directly seeded into Alice’s/Bob’s laser, each source station does provide an entry to enable transmission of the reference light into the theoretically protected space, interfering with Alice’s/Bob’s laser beam. The OPLL then acts as feedback to adjust the wavelength of Alice’s/Bob’s laser for mutual matching, ensuring identical optical fields with correlated phase. Our investigation reveals a loophole in wavelength-intensity correlation in the OPLL scheme. By exploiting this loophole, Eve can switch wavelengths of the reference light, thereby controlling its wavelength and indirectly affecting the mean photon number of quantum states prepared by Alice and Bob, while maintaining stable interference between them. This attack is referred to as a wavelength-switching attack. Surprisingly, under this scenario of a wavelength-switching attack, there is an increase in mean photon number by 8.7%, leading to insecurity of secret key.
Results
The idea of wavelength-switching attack
The fundamental mechanisms of TF-class QKD are elucidated in this section, providing insights into its superiority over the PLOB bound. Subsequently, the OPLL, as the pivotal component of TF-class QKD systems, is introduced in detail. Building upon this foundation, a specialized hacking method targeting TF-class QKD systems equipped with OPLL is proposed as the wavelength-switching attack.
TF-class QKD based on OPLL
The TF-class QKD protocol is an efficient variant of the MDI QKD protocol. In the original MDI QKD protocol, Alice and Bob each transmit a photon to Charlie for a two-photon Bell state measurement. In contrast, the TF-class QKD protocol achieves post-selected entanglement by performing single-photon interference at Charlie’s side instead of a two-photon Bell state measurement, enabling it to achieve a key rate proportional to the square root of channel transmittance (\(O(\sqrt{\eta })\)). To ensure successful single-photon interference at Charlie’s side, maintaining high coherence in the optical fields emitted by Alice and Bob becomes crucial. Consequently, ensuring wavelength consistency between Alice’s and Bob’s light sources becomes essential in implementing the TF-class QKD protocol.
To achieve correlated phase between two optical fields, Alice and Bob employ the OPLL structure in TF-class QKD systems for wavelength and phase synchronization, as depicted in Fig. 1(a). The OPLL comprises a frequency-locking controller (FLC), piezoelectric transducer (PZT), acousto-optic modulator (AOM), and heterodyne measurement. Charlie utilizes an ultra-stable laser to generate a reference light, which is subsequently transmitted to Alice and Bob. This reference light does not carry any encoding information but can be amplified through erbium-doped fiber amplifiers (EDFAs) during transmission. Upon receiving the reference light, Alice/Bob employs heterodyne measurement to determine the frequency/phase difference between her/his laser and the reference light. Specifically, a photodetector and phase discriminator detect the frequency/phase deviation, which is then processed by a proportional integrator (PI) controller to adjust Alice’s/Bob’s laser frequency/phase to match that of the reference light. This adjustment is achieved by controlling PZTs and two inserted AOMs in their respective lasers. The PZTs are used for adjusting initial frequencies and constraining slow frequency drifts while AOMs compensate for fast frequency shifts. When there is a change in the wavelength of the reference light, the FLC rapidly adjusts the frequency modulation via the AOM. Following this, to maintain the AOM in their optimal operating state, the FLC gradually alters the frequency modulation of the AOM back to its central value, while concurrently modifying the PZT to compensate for the frequency discrepancy. The coordinated operation of PZTs and AOMs enables precise frequency synchronization between Alice’s and Bob’s lasers in TF-class QKD systems.
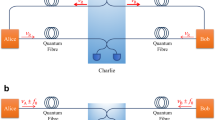
a Schematic diagram illustrating the structure of the OPLL in a TF-class QKD system, along with the corresponding wavelength-switching attack. The red and blue connecting lines represent optical fiber and electrical cables, respectively. The frequency-locking controller (FLC) modulates the operation of Alice’s /Bob’s piezoelectric transducer (PZT) and acousto-optic modulator (AOM2/AOM3) to ensure the coherence of optical field between Alice and Bob. The optical intensity of Alice’s /Bob’s laser is measured by photodetector PD5/PD6, whose bandwidth is 500 MHz, connected to an oscilloscope with sampling rate of 80 GSa/s. EDFAs, erbium-doped fiber amplifiers; BS, beam splitter; Het, heterodyne measurement; PMBS, polarization-maintaining beam splitter. b Interference measurements obtained by Charlie in the TF QKD system under both normal operation conditions and during the presence of a wavelength-switching attack at fΔ = 30 MHz. c Optical power measurements recorded at AOM2's output while subjected to a wavelength-switching attack with the rate of wavelength switching rs = 100 kHz.
The working principle of wavelength-switching attack
As previously mentioned, in TF-class QKD systems, the OPLL structure has been employed to ensure the coherence of optical fields between Alice and Bob16,17,20,21,22,23,34. However, the implementation of this structure introduces a potential vulnerability by creating an open port for the reference light to enter Alice’s/Bob’s lab under the assumption that it is well protected. This reference light could serve as a pathway for Eve to manipulate the internal devices of Alice and Bob, thereby compromising one of the fundamental assumptions of QKD - strict protection of internal devices. In line with addressing practical security concerns, this subsection presents how Eve can exploit this open port for manipulating Alice’s and Bob’s laser sources through a wavelength-switching attack aimed at compromising the security of TF-class QKD.
In the TF-class QKD system, exemplified by “TF-class QKD based on OPLL”, the OPLL structure facilitates precise adjustment of Alice’s or Bob’s laser wavelength through coordinated actions of AOM and PZT. Our primary focus lies in elucidating the operational procedure of OPLL and exploiting a loophole in the AOM within this configuration to control the output intensities of quantum states prepared by Alice and Bob. Specifically, we observe that any sudden fluctuations in wavelength trigger prompt corrective shifts by the AOM. However, an unforeseen imperfection arises from the dependence of insertion loss on modulation frequency faom, which is further illustrated in “Model of AOM”.
Based on the aforementioned concept, we propose a wavelength-switching attack for the TF-class QKD system, as depicted by the red area in Fig. 1(a). In this attack scenario, a wavelength-switching module consisting of an AOM1 and an arbitrary waveform generator (AWG) is inserted at the output of the reference laser, as shown in the red box in Fig. 1(a). Consequently, the AOM induces frequency shifts between faom1 and faom2, while the AWG controls the rate of wavelength switching (rs). By carefully adjusting these parameters, Eve ensures that only AOM operates without any adjustment on PZT in Alice’s/Bob’s OPLL module. Subsequently, she transmits a reference light with a pattern of switched wavelengths to both Alice and Bob. Upon receiving this reference light, Alice and Bob measure its heterodyne frequency relative to their local light source. The measurement reveals two peak values corresponding to different wavelengths of the reference light, prompting FLC to adjust AOM levels in Alice/Bob accordingly. In essence, Eve manipulates the wavelength of reference light to trigger wavelength switching in Alice’s/Bob’s local light sources. Importantly, this wavelength switching also reduces insertion loss in AOMs leading to increased intensity of quantum states prepared by Alice/Bob. If not monitored properly by Alice and Bob through their output light signals, this increased intensity could potentially enable Eve to eavesdrop on their secret key.
It should be noted that in a wavelength-switching attack, variations in insertion loss of AOM are determined by fΔ = ∣faom1 − faom2∣. Hence, when selecting a value for fΔ, Eve must ensure it is sufficiently large to cause a discernible change in mean photon numbers within quantum states generated by Alice and Bob. Moreover, adjustments to fΔ are constrained within limits defined by FLC and AOM’s maximum capabilities within OPLL. Subsequently, an experimental demonstration illustrating this wavelength-switching attack will be presented in order to emphasize its potential threat arising from unauthorized light infiltration into TF-class QKD source stations.
Experimental demonstration
In this wavelength-switching attack, Eve exploits the security vulnerability of the AOM in the OPLL module. Therefore, this section initially presents the calibrated characteristics of the AOM. Based on these calibration results, we determine the parameters required to conduct a wavelength-switching attack and demonstrate its impact on TF-class QKD later in this section.
The characteristics of the AOM
To investigate the characteristics of the AOM, a comprehensive test was conducted to examine its response under various input conditions, with a specific focus on two key dimensions: carrier frequency and driving voltage. Regarding the test on carrier frequency, a constant driving voltage of 15.84 V was applied to the AOM, and a sinusoidal driving signal with frequencies faom ranging from 0 to 240 MHz was injected into it. The initial laser wavelength, λin = v/fin = 1550 nm where v represents the speed of light in optical fiber and fin is the frequency. Upon receiving the driving signal, the AOM effectively modulates the light’s wavelength to \({\lambda }_{out}=v/\left({f}_{{\rm{in}}}+{f}_{{\rm{aom}}}\right)\). By continuously varying faom during the experiment, accurate characterization of how different values of faom corresponded to changes in output power was obtained. During testing on driving voltage, a fixed-frequency sinusoidal driving signal at 200 MHz was applied to the AOM while systematically adjusting peak-to-peak voltages within a range of 1 V to 15 V. This meticulous adjustment allowed for establishing an empirical relationship between variations in input voltage levels and corresponding changes in output efficiency for precise performance evaluation.
The relationship between AOM attenuation and frequency modulation is illustrated in Fig. 2a. In this subfigure, the black solid curve represents simulation results, while the red dots correspond to experimental measurements. The observed attenuation spans a range from over 50 dB to a few decibels as a function of modulation frequency. Notably, the minimum measured attenuation value for the AOM employed in this study is 3.57 dB, occurring at a modulation frequency of 195 MHz. This variation in attenuation primarily stems from the effective coupling of light within the AOM device and its piezoelectric transducer efficiency. Additionally, imperfect coupling may contribute to discrepancies between experimental data (red dots) and simulation results (black curve). Disregarding coupling efficiency reveals that higher modulation frequencies result in increased ultrasonic power, directly influencing output efficiency. For comprehensive details on the working principle and model of AOM, please refer to “Model of AOM”.
a The relationship between AOM attenuation and frequency modulation was characterized. b The relationship between AOM attenuation and driving voltage was characterized. The red upward/downward triangles represents that the driving voltage of AOM is 10.56 V/ 8.68 V. The input power of the AOM was 6.22 mW, and its model number is GST200.
The relationship between AOM attenuation and driving voltage is depicted in Fig. 2b. In the subfigure, the solid black curve represents the experimental measurements. The attenuation varies from over 25 dB to a few decibels with fluctuations in the driving voltage. The minimum observed attenuation value for the utilized AOM in this study is 3.59 dB, corresponding to a driving voltage of 15 V, and modulation frequency of 200 MHz. The fluctuation in attenuation primarily arises due to insufficient excitation of the piezoelectric transducer caused by decreasing voltage, resulting in inadequate ultrasonic power output.
Thus, in the TF-class QKD system under wavelength-switching attack, the attenuation of an AOM is influenced by both frequency modulation and drive voltage. For instance, when faom1 = 200 MHz, faom2 = 180 MHz, and, thus, fΔ = 20 MHz, Fig. 2a shows that frequency modulation results in an increase in attenuation by 0.69 dB. Meanwhile, Fig. 2b illustrates that the driving voltage is increased from 8.95 V (black dot) to 10.56 V (red upward triangle, high voltage), resulting in a 1.02 dB decrease in attenuation. The combined effect of these two factors ultimately leads to an overall attenuation reduction of 0.33 dB for the AOM, which is consistent with the measured value, as indicated in Fig. 2c when fΔ = 20 MHz. When the AOM2 (AOM3) work frequency returns to 200 MHz, Fig. 2b also illustrates that the driving voltage reduces to 8.68 V (red downward triangle, low voltage), resulting in a 0.14 dB increase in attenuation. Demonstration of wavelength-switching attacks with more details are presented in the following subsections.
Testing of wavelength-switching attack
In the tested TF QKD system, Alice/Bob employs a laser source with the linewidth of less than 0.1 kHz, whose output optical power ranges from 12 mW to 40 mW. Alice and Bob maintain a fixed light-frequency difference of 112 MHz between their local light and the reference light using an OPLL, whose locking bandwidth is 112 ± 30 MHz and the locking time is about 0.2 μs. Once the OPLL is locked, the response time of the FLC to control AOM is between 3 μs-10 μs. This identical frequency difference ensures that Alice and Bob have consistent frequencies with each other. Without any attack, as shown in Fig. 3a, a single peak of the heterodyne frequency appears at 112 MHz with a maximum power of −9.14 dBm. Under the wavelength-switching attack conducted by Eve as depicted in the red area in Fig. 1a, where there is a rapid change in the wavelength of the reference light, the heterodyne frequency is no longer fixed at 112 MHz. We consider a set of attack parameters where there is maximum wavelength change (fΔ = 30 MHz) and switching speed within the response range of FLC to control AOM (rs = 100 kHz). As shown in Fig. 3b, under this attack, two peaks appear at frequencies 112 MHz and 142 MHz, respectively. The difference between these two peaks depends on the introduced attack frequency (fΔ). Additionally, it can be observed from Fig. 3b that these two frequency peaks have power values of −15.14 dBm and −16.75 dBm, respectively. The measured peak power of heterodyne frequency under this attack still allows for proper functioning of OPLL since FLC only requires a minimum power greater than or equal to −30 dBm, which remains satisfied even under this specific attack.
In a TF-class QKD system, Charlie provides the reference light to Alice and Bob and performs interferometric measurements on the quantum signals they send back, as depicted by the blue area in Fig. 1a. Ensuring stable interference is crucial for successful interferometric measurement in order to achieve high visibility of quantum state detection. This step plays a critical role in establishing secure key generation between Alice and Bob within the TF-class QKD system. Therefore, it is essential to verify the stability of interference under wavelength-switching attacks. To maintain stable interference despite such attacks, Eve manipulates the wavelength of the reference laser while simultaneously affecting Alice’s and Bob’s lasers. The key lies in selecting an appropriate switching rate (rs) that achieves stable interference. Figure 1b illustrates Eve’s selection of four switching rates (rs) as attacking parameters. The black and red solid lines represent optical power measured by PD3 and PD4 at two output arms of Charlie’s interference setup respectively. When there is no attack (rs = 0), Charlie measures smooth and stable interference over time. However, slight fluctuations are observed when Alice’s and Bob’s wavelengths are switched at rates of either 100 kHz or 200 kHz, indicating potential disturbance caused by these attacks.
The slight fluctuations begin to decrease at the switching rate of 400 kHz. In this scenario, the response time of OPLL is surpassed by rs, rendering the OPLL incapable of promptly transmitting the frequency command. Consequently, two potential outcomes emerge: if the FLC fails to transmit the frequency shift command to Alice’s and Bob’s AOM, system security remains uncompromised; however, successful transmission of the frequency shift command by FLC to Alice’s and Bob’s AOM triggers an effective wavelength-switching attack. Subsequently, in following iterations of feedback loop, a sustained frequency shift can be maintained resulting in more stable interference compared to cases where rs = 100 kHz and rs = 200 kHz, as illustrated in Fig. 1b. Nevertheless, it should be noted that continuous operation of the frequency shift command on the AOM is not guaranteed. Gradually, this command is transferred from the AOM to PZT by FLC which reduces both wavelength shifting applied by AOM and optical intensity simultaneously. In summary, attacks at a switching rate of 400 kHz do not always exhibit stability or controllability.
The conducted experiment illustrates that, notwithstanding slight variations, the overall influence of a wavelength-switching attack on Charlie’s measured interference in a TF-class QKD system remains constrained. As a result, Eve can strategically adapt her wavelength switching rate according to real-time conditions for her benefit while minimally disturbing the functionality of the TF QKD system.
Gain of average photon number under attack
Consequently, we conduct a comprehensive investigation into the augmentation of the mean-photon number in Alice’s and Bob’s quantum states when subjected to a wavelength-switching attack. The magnitude of this augmentation serves as an indicator for quantifying the information intercepted by Eve from Alice and Bob, thereby providing crucial insights into potential eavesdropping on secure keys.
Experimental data in Fig. 1c illustrates the output power of Alice (Bob) with and without a wavelength-switching attack. In the absence of an attack, the optical power output of Alice or Bob remains relatively stable, as depicted in the leftmost chart in Fig. 1c. At this juncture, the driving voltage of the AOM is 8.9 V, indicated by the black dot in Fig. 2b. As fΔ increases, both Alice’s and Bob’s optical intensity experiences fluctuations during different phases of the switching cycle shown by the rest of charts in Fig. 1c. This behavior arises from energy storage characteristics inherent to TeO2 material used in AOMs36. With increasing fΔ values, ultrasonic power also rises correspondingly, leading to an increase in AOM voltage (indicated by red upward-pointing triangle marker in Fig. 2b). Conversely, when ultrasonic power decreases, so does the driving voltage of AOM (as shown by red downward-pointing triangle marker in Fig. 2b). It is noteworthy that increased optical power resulting from attacks represents a gain exceeding designed mean photon number for both Alice’s and Bob’s quantum states. The gain value can be calculated as increased optical power divided by designed optical power. Higher gain values imply greater benefits for Eve. From Fig. 1c, it can be inferred that under varying fΔ values such as 1 MHz, 3 MHz, 9 MHz, 20 MHz, and 30 MHz respectively; output gains for either Alice or Bob are found to be 0.86%, 1.63%, 3.19%, 4.04%, and 4.35%.
The correlation between the shifted wavelength under attack and the gain in mean photon number of emitted quantum states in the TF-class QKD system is illustrated in Fig. 4. The experimentally measured values after conversion are denoted by yellow markers. The gain in mean photon number of the TF-class QKD system exhibits a rapid increase when fΔ is less than or equal to 10 MHz. After that, the rate of increase slows down. The gain in mean photon number is maximized at fΔ = 30 MHz, beyond which the OPLL is no longer working in the locking status. Therefore, we limit our frequency shift to a maximum of 30 MHz and apply it simultaneously to the OPLLs of both Alice and Bob during the experiment. As a result, the mean photon number of Alice/Bob is increased by 4.35%, and the overall intensity gain is 8.7% for the whole TF QKD system as defined in ref. 6.
Effect on the security of TF-class QKD
The experiment demonstrates that the wavelength-switching attack can enhance the output power of Alice’s and Bob’s laser source, resulting in a factor of g = G + 1 > 1 for the mean photon numbers of all quantum states. Assuming that Alice’s and Bob’s photon numbers still follow a Poisson distribution, all μ values become \({\mu }^{{\prime} }=g\mu\) under the wavelength-switching attack. Consequently, it is necessary to theoretically evaluate the impact of this attack on the original TF QKD system. In this study, we present a comprehensive security analysis of the TF QKD system and extend our analysis to include the sending-or-not-sending TF QKD (SNS-TF-QKD) system.
Security analysis on TF QKD
In the TF QKD system, Alice and Bob generate phase-randomized optical fields, which are transmitted to Charlie through a quantum channel. Subsequently, Charlie performs the interferometric measurement and announces an event only if a single-photon detector is clicked. The event will be considered valid for generating a secure key if Alice and Bob select the same random phase. To evaluate the potential vulnerability of wavelength-switching attacks, we consider typical implementations where Alice/Bob uses three intensity settings \({\mu }_{a,b}\in \left\{{\mu }_{0}/2,{\mu }_{1}/2,{\mu }_{2}/2\right\}\), with μ0 = 0.4, μ1 = 10−2, and μ2 = 10−4. Here, μ0 represents the signal state while μ1 and μ2 represent decoy states. In scenarios with a realistic number of transmitted signals approaching asymptotic limits, it is possible to establish a lower bound on the secret key rate6.
where d = 0.5 is the duty cycle between the classical and the quantum modalities, M = 16 is the value of phase slices, \({Q}_{1,L}^{{\mu }_{0}}\) denotes a lower bound on the single-photon yield, e1,U denotes an upper bound on the phase error rate, f = 1.16 is the efficiency of error correction, \(Q^{\mu_{0}}\) represents the overall experimentally observed gain, \(E^{\mu_{0}}\) is the overall experimentally observed quantum bit error rate (QBER), and \({H}_{2}(x)=-x\,{\log }_{2}(x)-(1-x){\log }_{2}(1-x)\) is the binary Shannon entropy function.
To estimate, \(Q_{1,L}^{\mu_0}, Q^{\mu_{0}}\), e1,U and \(E^{\mu_0}\), one can use analytical or numerical tools. Here we have that
with \(\eta ={\eta }_{det}\times 1{0}^{-\frac{\alpha L/2}{10}}\), ηdet = 30% is total detection efficiency, α = 0.2 dB/km is the linear attenuation of a standard optical fibre, and L is the distance.
where
For the error rates,
with eopt = 3% is the channel optical error rate. In the presence of the wavelength-switching attack, Alice and Bob estimate e1,U, Y0,L, and Y1,L using Eq. (3) and Eq. (4), but now calculate \({E}^{{\mu }_{0,1,2}}\) and \({Q}^{{\mu }_{0,1,2}}\) using the experimentally observed parameters \({\mu }_{0,1,2}^{{\prime} }=g\times {\mu }_{0,1,2}\). We conduct a simulation analysis using parameters corresponding to a typical experiment22 to illustrate the security threat posed by a wavelength-switching attack on the TF QKD system. The results with and without an attack on the TF QKD system are depicted in Fig. 5. The black solid line represents the lower bound RL as defined by Eq. (1) under no attack conditions. Subsequently, we simulate the degradation of security bounds due to Eve’s wavelength-switching attack. Specifically, in Fig. 5, the red-dashed and blue-dotted lines respectively indicate values of incorrectly estimated (RL) by Alice and Bob when g = 1.087 in the presence of an attack. As shown in Fig. 5 compared to no-attack scenario represented by black solid line, the secure key rate (RL) given by red-dashed line is significantly higher. In other words, Alice and Bob overestimate their secure key rate in response to an attack. The gap between these two curves indicates that Eve can eavesdrop on a portion of the secure key rate without being detected while eventually deducing shared secure key between Alice and Bob.
In Fig. 6, we present the impact of the wavelength-switching factor fΔ on the lower bound of secure key rate at a fixed distance (560 km) and g = 1.087. The graph illustrates both incorrect and correct estimates of secure key rates for the TF QKD system under attack, represented by upward triangles and downward triangles respectively. In this scenario, an increase in parameter fΔ results in a higher mean photon number for quantum states prepared by Alice and Bob. This consistently elevated mean photon number leads to an overestimation of the lower bound RL of key rate, as indicated by the red-square markers, thereby widening the gap between overestimated and correct key rates illustrated by blue-dot markers. To summarize, wavelength-switching attacks cause Alice and Bob to overestimate their key rate, compromising the security of a TF QKD system.
Security analysis on SNS-TF-QKD
Next, we consider the case of SNS-TF-QKD10. Similar to the previous example, it is assumed that both Alice and Bob employ three distinct intensities, namely μ0, μ1, and μ2. In the finite-key case, the lower bound for the secure key rate can be derived from refs. 23,37,38.
where N represents the finite size, n1 denotes the lower bound of the number of survived untagged bits, \({e}_{1}^{ph}\) gives the upper bound of the phase-flip error rate for those survived untagged bits, f is the error correction inefficiency, nt is the number of survived untagged bits, Ez is the corresponding bit-flip error rate in those survived bits, and γ, which takes logarithmically small values, is for security considerations with finite-data size and advanced decoy state analysis.
To evaluate Eq. (6), Alice and Bob need to calculate the lower bound of the expected value of the counting rate of untagged photons
where \({S}_{jk}\left(jk=\left\{00,10,01,20,02\right\}\right)\) denotes the counting rate of source jk37. In the wavelength-switching attack, the parameters Sjk should be calculated based on the experimentally obtainable data \({\mu }_{0}^{{\prime} }\), \({\mu }_{1}^{{\prime} }\), and \({\mu }_{2}^{{\prime} }\). According to ref. 23,37, n1 and nt can be obtained from S1,L, Ez can be calculated based on Sjk, and \({e}_{1}^{ph}\) can be estimated from e1,U. The upper bound of the expected value of the phase-flip error rate satisfies39
where TΔ is the effective rate of detectors. Furthermore, we can obtain a much lower QBER Ez in those survived bits by applying active odd-parity pairing40,41,42 to the above method.
We adopt a methodology similar to that employed in the preceding subsection to assess RL under the presence of a wavelength-switching attack. We employ parameters from a representative case23 for simulation purposes. For simplicity, we assume Eve executes a symmetric attack by injecting identical wavelength-switching light into both Alice and Bob. The resulting lower bound on the key rate is depicted in Fig. 7. In this example, we consider two potential values for the gain factor, namely g = 1 and g = 1.087. The scenario with g = 1 corresponds to an absence of attacks. Evidently, the incorrect secure key estimated by Alice and Bob in the presence of an attack surpasses the correct value.
Discussion
Countermeasures
Our experimental results indicate that the TF QKD employed by the external reference-light-based OPLL is vulnerable to wavelength-switching attacks. An eavesdropper can manipulate Alice’s and Bob’s output photon numbers by altering the wavelength of the reference light, compromising the practical security of TF-class QKD systems. Consequently, it is imperative to develop countermeasures against such attack.
The observed variation in the intensity of quantum states is attributed to the change in optical insertion loss. This change is mainly because the AOM receives an uncharacterized frequency modulation and insufficient driving voltage when the FLC adjusts it to match the reference light’s wavelength switching as analyzed in “The characteristics of the AOM”. Being immune to the wavelength-switching attack, we propose a calibration procedure for the AOM before system operation to minimize the insertion loss due to driving voltage. In step 1, the driving voltage of the AOM is scanned under a fixed modulation frequency to determine the optimal voltage value, Vo, corresponding to the minimum insertion loss at this certain modulation frequency. In step 2, the modulation frequency of the AOM is scanned with Vo found in Step 1, obtaining the optimal frequency Fo, corresponding to the further minimized insertion loss. Afterwards, Vo and Fo are set as the basic parameters for the FLC to control the AOM. This process ensures that the wavelength-switching attack will only increase the insertion loss of the OPLL, thus mitigating the associated security risks.
An additional countermeasure could be involving monitoring devices to detect eavesdropping. For example, during heterodyne measurements, photodetectors PD1 and PD2 might be used to identify multiple peaks in the spectrum, potentially indicating a wavelength-switching attack. Moreover, by monitoring the intensity with PD5 and PD6 in the source stations, the system can monitor the intensity fluctuation of Alice’s and Bob’s output light. These fluctuations can be indicative of the potential wavelength-switching attack. From another aspect of view, inspired by the fully passive QKD protocol43,44, the vulnerability related to wavelength-switching attacks might be mitigated if the wavelength/optical field of a laser source can be passively modulated or locked.
An alternative approach for Alice and Bob to counter the wavelength-switching attack is to modify the configuration of the TF QKD system by employing a local frequency reference. In this way, Alice/Bob in the TF-class QKD system does not open a door for any untrusted party, fundamentally eliminating the security threat introduced by the external reference light. Recent research has proposed a practical method that utilizes the saturated absorption spectroscopy of acetylene as an absolute reference, thereby eliminating the need for external reference light in TF-class QKD implementation35. This method indeed can prevent Eve from using external reference light to attack the TF-class QKD system. However, integrating acetylene as a new component may introduce potential risks that necessitate further investigation.
Conclusion
The TF-class QKD has been demonstrated to surpass the fundamental rate-distance limit, which necessitates the generation of identical optical fields by two independent lasers located at separate positions for Alice and Bob. In current implementations, a third-party reference light is commonly employed to lock the wavelengths of the lasers in order to achieve matching. Although this reference-light-locking structure does not directly contribute to key generation, it introduces a potential vulnerability that can be exploited by an eavesdropper, posing a security risk to the devices used by Alice and Bob. This study unveils a wavelength-switching attack on the TF-class QKD system employing an optical OPLL structure. Experimental results demonstrate that Eve can exploit this attack to reduce attenuation in the AOM of the TF-class QKD system, causing optical power from Alice and Bob to exceed intended levels. Importantly, this attack challenges fundamental assumptions in TF-class QKD protocols regarding mean photon number of prepared quantum states and well-protected source stations. Despite altering wavelengths of lights emitted by Alice and Bob, these hacked source units remain consistent, enabling stable interference at Charlie’s location. Theoretical analysis conducted on both TF QKD protocol and SNS-TF-QKD protocol indicates that the wavelength-switching attack could significantly compromise security in implementation of TF-class QKD - legitimate users overestimate secure key rates when facing such attacks. Since this attack is due to imperfect calibration in the external-reference-locking configuration, we propose countermeasures via loss-minimization calibration or using no-external-reference-light scheme35,45,46,47,48. The possibility of this attack on various OPLLs schems shall be experimentally verified in the future. Additionally, the practical security of other variants of TF-QKD, such as phase-matching QKD9, shall be investigated as future study.
Methods
Model of AOM
The AOM device operates by converting electrical energy into ultrasonic vibrations. Adjusting the modulation frequency in this process directly affects the electrical energy, thereby influencing the wavelength and intensity of light within an acoustic-optic medium. To provide a clearer explanation, we have employed a simplified model as depicted in Fig. 8a to establish a direct correlation between modulation frequency and AOM attenuation values in this specific context. This approach facilitates a more accessible comprehension of the interrelationship among key factors in our study.
The input optical intensity of the AOM, denoted as \({P}_{aom}^{{\rm{in}}}\), is set at 6.22 mW in the given scenario. The output optical intensity, \({P}_{aom}^{{\rm{out}}}\), can be expressed as \({\eta }_{aom}{P}_{aom}^{{\rm{in}}}\), where ηaom represents the diffraction efficiency of the acousto-optic medium used in the AOM. Moreover, to simplify the simulation, we introduce δaom as a fixed value of 3.57 dB to account for other attenuations. It should be noted that this parameter may vary experimentally due to factors such as coupling ratio and practical considerations. Mathematically, the diffraction efficiency (ηaom) can be mathematically expressed as follows49:
where λ = 1550 nm is the wavelength of light. Maom,2 is the acousto-optic figure of merit for the crystal.
Hpt and Lpt correspond to the thickness and length of the piezoelectric transducer, respectively, as shown in Fig. 8b. Paom,a is the ultrasonic power, which can be written as
where Faom is the relative frequency. faom is the modulation frequency. faom,0 is the half wavelength frequency of the piezoelectric layer. Zaom,M is the relative acoustic impedance of the acousto-optic interaction medium.
The AOM depicted in Fig. 8b is composed of glass ceramics and features a TeO2 composition, which is well-known for its ability to minimize scattering losses at the interfaces between glass and crystal. This characteristic makes it an exceptional host material for precipitating crystalline phases36. The value of Maom,2 for this medium has been measured at 34.7 × 10−15 s3/kg49. Moreover, this medium exhibits energy storage properties that make it highly suitable for advanced electronic applications such as electric microchips, hybrid vehicles, and pulse power systems50,51,52. In essence, when subjected to increasing ultrasonic power Paom,a, TeO2 rapidly charges up while effectively suppressing excessive energy; conversely, it releases stored energy during power decrease.
Data availability
The data that support the findings of this study are available from the corresponding author upon request.
Code availability
The codes used for numerical analysis are available from the corresponding author upon request.
References
Bennett, C. H. & Brassard, G. Quantum cryptography: public key distribution and coin tossing. Theor. Comput. Sci. 560, 7–11 (2014).
Xu, F., Ma, X., Zhang, Q., Lo, H.-K. & Pan, J.-W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 92, 025002 (2020).
Archana, B. & Krithika, S. Implementation of bb84 quantum key distribution using optsim. In Proc. 2nd International Conference on Electronics and Communication Systems (ICECS), 457–460 (IEEE, 2015).
Pirandola, S., Laurenza, R., Ottaviani, C. & Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 8, 15043 (2017).
Takeoka, M., Guha, S. & Wilde, M. M. Fundamental rate-loss tradeoff for optical quantum key distribution. Nat. Commun. 5, 5235 (2014).
Lucamarini, M., Yuan, Z. L., Dynes, J. F. & Shields, A. J. Overcoming the rate-distance limit of quantum key distribution without quantum repeaters. Nature 557, 400–403 (2018).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108, 130503 (2012).
Curty, M. et al. Finite-key analysis for measurement-device-independent quantum key distribution. Nat. Commun. 5, 3732 (2014).
Ma, X., Zeng, P. & Zhou, H. Phase-matching quantum key distribution. Phys. Rev. X 8, 031043 (2018).
Wang, X.-B., Yu, Z.-W. & Hu, X.-L. Twin-field quantum key distribution with large misalignment error. Phys. Rev. A 98, 062323 (2018).
Cui, C. et al. Twin-field quantum key distribution without phase postselection. Phys. Rev. Appl. 11, 034053 (2019).
Curty, M., Azuma, K. & Lo, H.-K. Simple security proof of twin-field type quantum key distribution protocol. npj Quantum Inf. 5, 64 (2019).
Yin, H.-L. & Chen, Z.-B. Finite-key analysis for twin-field quantum key distribution with composable security. Sci. Rep. 9, 17113 (2019).
Currás-Lorenzo, G. et al. Tight finite-key security for twin-field quantum key distribution. npj Quantum Inf. 7, 22 (2021).
Minder, M. et al. Experimental quantum key distribution beyond the repeaterless secret key capacity. Nat. Photonics 13, 334–338 (2019).
Liu, Y. et al. Experimental twin-field quantum key distribution through sending or not sending. Phys. Rev. Lett. 123, 100505 (2019).
Chen, J.-P. et al. Sending-or-not-sending with independent lasers: Secure twin-field quantum key distribution over 509 km. Phys. Rev. Lett. 124, 070501 (2020).
Zhong, X., Wang, W., Qian, L. & Lo, H.-K. Proof-of-principle experimental demonstration of twin-field quantum key distribution over optical channels with asymmetric losses. npj Quantum Inf. 7, 8 (2021).
Pittaluga, M. et al. 600-km repeater-like quantum communications with dual-band stabilization. Nat. Photonics 15, 530–535 (2021).
Liu, H. et al. Field test of twin-field quantum key distribution through sending-or-not-sending over 428 km. Phys. Rev. Lett. 126, 250502 (2021).
Chen, J.-P. et al. Quantum key distribution over 658 km fiber with distributed vibration sensing. Phys. Rev. Lett. 128, 180502 (2022).
Wang, S. et al. Twin-field quantum key distribution over 830-km fibre. Nat. Photonics 16, 154–161 (2022).
Liu, Y. et al. Experimental twin-field quantum key distribution over 1000 km fiber distance. Phys. Rev. Lett. 130, 210801 (2023).
Liu, Y. et al. 1002 km twin-field quantum key distribution with finite-key analysis. Quantum Front. 2, 16 (2023).
Zhong, X., Hu, J., Curty, M., Qian, L. & Lo, H.-K. Proof-of-principle experimental demonstration of twin-field type quantum key distribution. Phys. Rev. Lett. 123, 100506 (2019).
Fang, X.-T. et al. Implementation of quantum key distribution surpassing the linear rate-transmittance bound. Nat. Photonics 14, 422–425 (2020).
Shor, P. W. & Preskill, J. Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85, 441–444 (2000).
Renner, R. Security of quantum key distribution. Int. J. Quantum Inf. 6, 1–127 (2008).
Sun, S.-H. et al. Effect of source tampering in the security of quantum cryptography. Phys. Rev. A 92, 022304 (2015).
Huang, A. et al. Laser-seeding attack in quantum key distribution. Phys. Rev. Appl. 12, 064043 (2019).
Pang, X.-L. et al. Hacking quantum key distribution via injection locking. Phys. Rev. Appl. 13, 034008 (2020).
Lu, F.-Y. et al. Hacking measurement-device-independent quantum key distribution. Optica 10, 520 (2023).
Ye, P. et al. Induced-photorefraction attack against quantum key distribution. Phys. Rev. Appl. 19, 054052 (2023).
Wang, S. et al. Beating the fundamental rate-distance limit in a proof-of-principle quantum key distribution system. Phys. Rev. X 9, 021046 (2019).
Chen, J.-P. et al. Twin-field quantum key distribution with local frequency reference. Phys. Rev. Lett. 132, 260802 (2024).
de Oliveira, R. C., Silva, A. C. A., Dantas, N. O., Mendez-González, Y. & Guerra, J. D. S. Physical properties and energy storage performance of teo2-based ferroelectric glass-ceramics. Ferroelectrics 611, 48–59 (2023).
Jiang, C., Yu, Z.-W., Hu, X.-L. & Wang, X.-B. Unconditional security of sending or not sending twin-field quantum key distribution with finite pulses. Phys. Rev. Appl. 12, 024061 (2019).
Hu, X.-L., Jiang, C., Yu, Z.-W. & Wang, X.-B. Universal approach to sending-or-not-sending twin field quantum key distribution. Quantum Sci. Technol. 7, 045031 (2022).
Yu, Z.-W., Hu, X.-L., Jiang, C., Xu, H. & Wang, X.-B. Sending-or-not-sending twin-field quantum key distribution in practice. Sci. Rep. 9, 3080 (2019).
Xu, H., Yu, Z.-W., Jiang, C., Hu, X.-L. & Wang, X.-B. Sending-or-not-sending twin-field quantum key distribution: Breaking the direct transmission key rate. Phys. Rev. A 101, 042330 (2020).
Jiang, C., Hu, X.-L., Xu, H., Yu, Z.-W. & Wang, X.-B. Zigzag approach to higher key rate of sending-or-not-sending twin field quantum key distribution with finite-key effects. New J. Phys. 22, 053048 (2020).
Jiang, C., Hu, X.-L., Yu, Z.-W. & Wang, X.-B. Composable security for practical quantum key distribution with two way classical communication. New J. Phys. 23, 063038 (2021).
Hu, C., Wang, W., Chan, K.-S., Yuan, Z. & Lo, H.-K. Proof-of-principle demonstration of fully passive quantum key distribution. Phys. Rev. Lett. 131, 110801 (2023).
Lu, F.-Y. et al. Experimental demonstration of fully passive quantum key distribution. Phys. Rev. Lett. 131, 110802 (2023).
Zhou, L., Lin, J., Jing, Y. & Yuan, Z. Twin-field quantum key distribution without optical frequency dissemination. Nat. Commun. 14, 928 (2023).
Zhou, L. et al. Experimental quantum communication overcomes the rate-loss limit without global phase tracking. Phys. Rev. Lett. 130, 250801 (2023).
Li, W. et al. Twin-field quantum key distribution without phase locking. Phys. Rev. Lett. 130, 250802 (2023).
Zhu, H.-T. et al. Experimental mode-pairing measurement-device-independent quantum key distribution without global phase locking. Phys. Rev. Lett. 130, 030801 (2023).
Kuanxin, Y., Xiaohong, D. & Zhaoguang, P. Principles and Devices of Acousto-Optics (Science Press, 2011).
Tian, J. et al. Dielectric characterization of a novel bi2o3-nb2o5-sio2-al2o3 glass-ceramic with excellent charge-discharge properties. J. Eur. Ceram. Soc. 39, 1164–1169 (2019).
Du, X. et al. Enhanced energy storage and discharge-charge performance by changing glass phase content in potassium sodium niobate glass-ceramics. Ceram. Int. 46, 11492–11498 (2020).
Khalf, A. Z. Ferroelectric Glass-Ceramic Systems for Energy Storage Applications (IntechOpen, 2020).
Acknowledgements
We thank X.-B. Wang, Q. Zhang, and C. Jiang for valuable discussions. This work was funded by the Innovation Program for Quantum Science and Technology (2021ZD0300704) and National Natural Science Foundation of China (Nos. 62371459 and 62061136011).
Author information
Authors and Affiliations
Contributions
Q.P., J.P., and A.H. conducted the experiment. T.X., D.W., and Y.W. support the experimental conduct. Q.P., Y.L., and A.H. analyzed the data. Q.P. and A.H. wrote the paper with input from all authors. A.H. and Y.L. supervised the project.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Peng, Q., Chen, JP., Xing, T. et al. Practical security of twin-field quantum key distribution with optical phase-locked loop under wavelength-switching attack. npj Quantum Inf 11, 7 (2025). https://doi.org/10.1038/s41534-025-00963-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41534-025-00963-9