Abstract
The Crucial and costly process of verifying medical documents frequently depends on centralized databases. Nevertheless, manual validation of document verification wastes a great deal of time and energy. The application of Blockchain technology could potentially alleviate the problem by reducing fraud and increasing efficiency. Non-transferable Soul-bound tokens (SBTs) can be a safe and unbreakable way to authenticate medical records by generating encrypted code, which allows the user to authenticate a portion of data. Within the paper, we provide a blockchain-based SBT-based automatic mechanism for authentication and verification of records. Soul-bound tokens generate a decentralized, immutable identity or credential system that is tied to a record. Through cloud computing, the system can reduce the verification time by accessing a decentralized database. Blockchain systems can lower platform costs and determine the optimal allocation of resources across a dispersed network by utilizing deep learning algorithms. Two advantages of utilizing blockchain technology are less fraud and increased efficiency. SBTs and cloud computing enable the procedure to be expedited and decentralized databases to be readily available. The suggested system’s scalability and potential uses in other industries may be the subject of future research.
Similar content being viewed by others
Introduction
Although there are various well-established methods for confirming medical information, detecting changed or fake documents remains a major challenge for the Web2 industry. There is an extreme requirement for cutting-edge automated technology. Model selection and training data needs are important factors when incorporating deep learning algorithms into blockchain-based secure electronic health records (EHRs). Both Quantity and Quality of Data1. In Quality, data is necessary for deep learning to function. EHR data needs to be precise, comprehensive, and reliable. Inaccurate or missing data can cause the model to perform poorly and produce predictions that are not trustworthy. Quantity: In deep learning models to learn efficiently, a lot of data is usually needed2. A sizable dataset is required to capture the subtleties of medical illnesses, treatments, and results due to the complexity of healthcare data. In Diverse Data, Diversity in Demographics: To guarantee that the model functions effectively across a variety of populations, training data should cover a broad range of demographic categories (age, gender, and race). In Clinical Diversity, the dataset to generalize successfully to varied clinical contexts, should include a range of medical illnesses, treatments, and outcomes.
Selection of models: an examination
Model building deep learning algorithms
Task complexity should be taken while selecting a model architecture, such as Recurrent Neural Networks (RNNs), or Convolutional Neural Networks (CNNs). For example, RNNs or Transformers are appropriate for sequential data (e.g., patient records across time), whereas CNNs work well with picture data (e.g., medical imaging). The aim is to establish a safe, effective, and focused healthcare system using healthcare providers can ensure secure data sharing, interoperability, and transparency while maintaining patient privacy and data integrity.
Scalability: The model must be scalable to manage complicated calculations and big datasets without causing undue latency, particularly when combined with a blockchain system.
Comprehending and Perceivability:
-
Interpretability: Models must be able to be understood by healthcare applications. In situations when comprehending the decision-making process is essential, models such as decision trees or more basic neural networks may be chosen.
-
Explainability Tools: Using explainability tools (like SHAP and LIME) can make easier for physicians to comprehend and believe the predictions made by a more complicated model.
The actions and states of a deep learning system can be documented on the blockchain. A multi-layered strategy that takes advantage of both technologies’ advantages is needed to integrate deep learning algorithms into blockchain-based secure electronic health records (EHRs) and improve data security, integrity, and usability in healthcare systems. Since multiple agents can work together to learn and make decisions, might pave the way for decentralized algorithms for reinforcement learning. Access to accurate, real-time healthcare services should be easy, smooth, and provided by a variety of features and services; the purpose of smart healthcare technology3. The security and care with which these services deal with sensitive health information is of the utmost importance. Token is created by blockchain technology and can be transferred between users. When comes to digital art and collectibles, NFTs are a great way to prove ownership. As an extension of NFTs, soulbound tokens (SBTs) aim to be linked to a specific individual or group and are not transferable. Just like other NFTs, SBTs can be publicly seen, and stored in an online wallet. There is no value in investing in SBTs. According to Weyl et al. (2022), have the potential to represent the holder’s affiliations, qualifications, commitments, and other attributes. Individuals can authenticate themselves using their authentic Web identities by utilizing SBTs provided by entities such as governments, businesses, and healthcare facilities3. Allows other parties to easily and quickly verify the information without needing the issuer’s help. Under investigation is a system that would allow any organization, be a government agency, medical facility, or other entity, to issue soul-bound tokens as a means of verifying the legitimacy of reports, medical prescriptions, or any other kind of document.
Soul-bound Tokens (SBT): The purpose of implementing SBT was to safeguard health records by preventing the shift of sensitive medical information. The patient’s private wallet and identity are the only things that SBTs are linked to, and that are non-transferable. To the owner of the token belongs full authority over their qualifications, reputation, and medical history. Soul-bound tokens can be used to validate any individual’s medical records because that are non-transferable and issued on the blockchain. As said earlier, Binance is the one that employs the technology of soul-bound tokens. In September 2022, Binance started offering clients tokens that were connected to their accounts. Minting BAB is a breeze for Binance users after that are verified their identities. Using a combination of public and private data, SBTs may construct a user’s social network. SBT attributes stand in for the data. A distinct class of blockchain-based tokens known as Soulbound Tokens (SBTs) is distinguished from standard tokens in several significant ways:
SBT differ from other tokens
SBTs: Innate Because tokens are by nature non-transferable, cannot be moved from one wallet to another after then have been issued to one. The tokens’ original receiver is guaranteed to keep them thanks to their non-transferability.
-
Conventional tokens, such as NFTs and cryptocurrencies, can be bought, sold, or exchanged on different platforms because that are usually transferable.
-
Safety and Secrecy:
-
SBTs: SBTs lower the possibility of identity and personal credential fraud or theft because that are non-transferable. As all are connected to a particular person’s wallet, that may also be more private.
-
Other Tokens: When moving between wallets, transferable tokens might raise privacy issues if transactions are not appropriately anonymized. Then are also more likely to be misplaced or stolen.
-
Role in medical record authentication:
-
Unchangeable Identity Confirmation: Using SBTs, a patient’s identification can be preserved in an unchangeable, safe manner. The danger of identity theft and fraud can be decreased by having each SBT include validated credentials attesting to the patient’s identity and medical background.
-
Uninterrupted Access to Health Records: Only those with permission can view a patient’s medical history thanks to the ability to link medical information to SBTs. Patient privacy can be preserved while streamlining the exchange of medical data between healthcare providers.
Counterfeit Medical Certifications: SBTs can be used by healthcare practitioners to confirm their qualifications and licences. To preserve the integrity of medical practice and guarantee that only competent people give medical care, these tokens can be used as evidence of training and specialization. Health Card Token (HCT): As a kind of ownership proof and medium of exchange, HCT is held by patients. The construction guarantees security and uniqueness by adhering to the ERC721 standard for NFTs. The three positions that create HCT are Owner (administration), Minters (doctors), and Users/Patients4. Some properties might be accessible only to authorized users due to their encryption, while others could be open to everybody. The data that the SBT issuer wants to disseminate via SBTs is entirely up to them. Below, you will find the Tokens shown in Fig. 1:
Problem statement
In the current healthcare landscape, Electronic Health Records (EHRs) are susceptible to illegal access, security lapses, and data manipulation. Instances of data breaches and cyber-attacks have raised serious concerns. The existing methods for securing EHRs, such as encryption and access controls, have limitations in providing a comprehensive and tamper-proof solution while the CF computation can be time-consuming when numerous sensors are used, and does not ensure that the best outcome is generated every time. Even though there is less duplicate data in the task, anomalous (faulty) data persists, and the clustering procedure is useless. indicates significant bandwidth and energy consumption for CHs5. Medical record management and verification are made strong and secure by blockchain technology. Numerous issues with conventional medical document management systems are addressed by immutability, decentralized access, better security, and interoperability characteristics. Healthcare providers may guarantee the availability, confidentiality, and integrity of medical records by utilizing blockchain technology, which will eventually improve patient care and operational effectiveness. There is a critical need for a robust, transparent, and decentralized system. The clustering procedure fails because the CF computation might take a long time when a large number of sensors are used, and it does not ensure that the best solution is always found. Although this effort reduces the amount of duplicate data, anomalous (faulty) data remains. This implies considerable energy and bandwidth use for CHs.
Research aims to address the following challenges:
-
Data Security: Develop a Blockchain-based architecture that ensures security, and confidentiality of patient records, protecting them from unauthorized access and cyber threats.
-
Data Integrity: Design mechanisms to guarantee the immutability and integrity of healthcare records, preventing unauthorized modifications and ensuring the accuracy of patient information.
-
Interoperability: Create a standardized and interoperable Blockchain solution may easily incorporate into the current healthcare systems, fostering collaboration and data exchange among different entities in the healthcare ecosystem.
-
Patient Privacy: Implement privacy-preserving features to empower patients with control over their own health data, adhering to regulatory requirements and ethical standards.
-
Scalability: Address the scalability challenges associated with Blockchain technology to ensure feasibility for large-scale healthcare systems, accommodating the growing volume of electronic health data.
-
Decentralization: Instead of being kept on a single, central server, a decentralized blockchain distributes the ledger.
-
Immutability: A transaction is said to be immutable if kept on the ledger and not able to be altered or eliminated.
-
Transparency: By enabling everyone on the network to view and validate the complete transaction history, blockchain technology promotes transparency.
Significance of research
The significance of scope in a Blockchain-Based Framework for Interoperable Electronic Health Records is multi-dimensional. The foundation for defining the objectives, challenges, and potential impacts of implementing blockchain technology in healthcare. A well-defined scope ensures that the framework addresses key issues like interoperability, security, privacy, cost efficiency, and scalability, ultimately leading to an improved, patient-centric healthcare system. As blockchain technology evolves, refining the scope will be crucial to leveraging full potential and enabling continuous innovation in healthcare. An unchangeable and transparent ledger for medical records is guaranteed by blockchain technology. By providing a history of patient data that is auditable and impenetrable. Administrative procedures have the potential to change how businesses and governments run, including increased productivity, cost savings, interoperability, and integration6,7. By offering a tamper-resistant and auditable history of patient data, enhances the system’s credibility by lowering the possibility of fraudulent activity.
-
Uncentralized Access Management: The study investigates the use of blockchain smart contracts to construct decentralized access control systems. The method enables precise management of who has access to medical records.
-
Data Integrity and Interoperability: The blockchain-based system’s design takes healthcare data interoperability into account. The project intends to establish a system that facilitates trustworthy and easy data sharing between healthcare providers by using standardized protocols and the blockchain’s consensus mechanism to ensure data integrity.
-
Adaptability to Cyberthreats: The study investigates how the decentralized nature of blockchain can lessen risks associated with centralized databases, hence enhancing the resilience of healthcare systems against cyber assaults. The covers defense against data manipulation, ransomware assaults, and other nefarious activities.
-
Ownership and Empowerment of Users: Ownership of health data and user empowerment are prioritized in the proposed system. Patients now possess greater authority over electronic health records (EHRs) by using blockchain technology, allowing or removing access as needed. It helps to make healthcare record management more patient-centric.
-
Optimizing performance and scalability: Investigates novel ways to maximize system performance without sacrificing security.
-
Adherence to Regulations: The design ensures that the suggested blockchain-based solution complies with current legal and ethical frameworks governing the management of electronic health records by considering compliance with healthcare regulatory requirements.
“ Blockchain-Based Framework for Interoperable Electronic Health Records for an Improved Healthcare System” is a research contribution that seeks to further the state of healthcare data security by offering a framework for the development of patient-centered, transparent, and safe electronic health record systems.
Contribution
The main contribution of the paper focuses on high-security, low latency, energy-efficient health monitoring is listed as follows:
-
To collect data without any congestion, implemented dual sinks, including an emergency sink and a periodic sink. Without delay, the health center receives all essential packets. Using the extended PRESENT approach, all patients who require healthcare monitoring are registered with the key management server (KMS).
-
Using the spotted hyena optimizer (SHO), node residual energy, transmission power, bandwidth, and signal-to-noise ratio (SNR) are used to calculate the best objective function (BOF), which is then used to construct clustering.
-
By examining the records, defective data packets are eliminated in the sink, which reduces bandwidth and energy usage. The patient’s body sensors are used to pick the next node if the CH is no longer able to communicate the data. In addition to choosing the best channel for the two remaining medical packet types based on RSS, SNR, channel capacity, and the radio power, the idle channel is used for emergency packet transmission. Consequently, interference was removed.
-
Every typical data packet is transferred using multihop transmission, taking into account factors like data rate, packet size, needed latency, data traffic type, and TTL. The best forwarders are chosen for a multihop data routing strategy that takes into account the distance to the CH, RSS, node residual energy and path duration.
-
The deep reinforcement learning system is used to sense and classify the surroundings and medical data for every patient. Compared to the traditional Markov model, suggested two stream-DNN in DRL.
-
To encrypt crucial and medical data that is sent straight to the CH and subsequently to the PBA, suggest the PRESENT method. In conclusion, data packets are archived in cloud servers and the blockchain according to the type of packet sensing.
Literature review
Blockchain technology’s data sharing, decentralization, and security benefits are examined, as well as potential applications in business, e-government, smart governance, and healthcare8. The report also discusses the limitations of traditional record-keeping and how blockchain technology may help. Blockchain technology is being studied in healthcare to improve data integrity, classify medical pictures, anticipate diseases, and stop drug counterfeiting in supply chain management. The article also discusses Soul bound tokens, which are digital tokens that can verify a person’s identity or ownership of an item. Soul bound tokens can replace centralized digital document verification. The literature analysis provides a solid foundation for the research study and highlights how deep learning and blockchain technology might improve medical document verification efficiency, security, and accuracy. Blockchain technology aims to create a decentralized, unsupervised system (Yli-Huumo et al., 2016). Used in business, e-government, smart government, and healthcare due to benefits (Sidhu, 2017, pp. 1–6; Hou, 2017, pp. 1–4; Arendsen et al., 2011). Deep learning, which can be learned from data, is based on artificial neural networks and is utilized in cybersecurity, text analytics, healthcare, and image identification. Blockchain can offer safe and accurate results. Machine learning requires enough reliable data. Studied blockchain technology for cloud computing security and trust. The study seeks to investigate how blockchain technology might create a distributed and decentralized trust architecture that improves cloud transaction integrity and traceability. Traditional record-keeping requires large storage facilities and can be difficult to obtain documents. The public cannot access these medical records. Medical records should be available to patients or authorized caretakers. Jamil et al. (2019) studied how blockchain technology might prevent drug counterfeiting in supply chain management. The innovative blockchain system captures the safe and transparent transit and handling of drugs from producer to patient, improving drug supply chain efficacy and safety. Umamaheswaran et al. polled 150 machine learning and blockchain experts in medicine to explore their healthcare applications (2022). Medical picture categorization, disease prediction, and blockchain data integrity improved in the study. BinDaaS (Bhattacharya et al., 2019, pp. 1242–1255) uses deep learning algorithms and blockchain technology to share EHR between several healthcare providers9,10,11,12. A public blockchain allows anybody to join and verify Soul-bound tokens. A multi-layered strategy that takes advantage of both technologies’ advantages is needed to integrate deep learning algorithms into blockchain-based secure electronic health records (EHRs) and improve data security, integrity, and usability in healthcare systems.
Since anybody may verify digital papers, the system is more transparent and decentralized. It may be less secure because relies on network security rather than a more restricted group of entities. Then showed a multi-chain application that covers inclusive governance, asset recovery, data integrity, and identity security in decentralized networks. Offer under-collateralized lending so borrowers can get loans while retaining a trustworthy web presence. The NFT ecosystem relies on non-fungible token marketplaces (NFTM), which pose security vulnerabilities. Das et al. presented NFT exchange on NFTM Dapp platforms in 202113,14,15. The process is full of security risks. Have discussed the potential that Open Sea and Rarible NFTs are fake. When an NFT is advertised, the NFTM seizes the token, allowing the seller to sell to the buyer. The NFTM must own, own, or operate the NFT. The escrow model is risky because all platform assets are housed in a single NFTM-managed escrow contract or wallet.
The security of the escrow contract or the external account that controls determine the security of all marketplace assets (Das et al., 2021). Verifiable credentials (VCs) and decentralized identifiers (DIDs), the technology used to create digital identities, are not standardized, allowing user data leakage and composability issues. A negative reputation and irreversible “scarlet letter” consequences now threaten users. SBTs, however, are still being defined and may offer additional protection and resilience to these threats (Jain et al., 2022). The security and authorization issues with IoT network access control are intended to be resolved by the suggested architecture. The system also aims to accomplish authorization, encryption, and security for the exchange of data over Internet of Things networks. Article presents a new approach to data sharing for Internet of Things devices that incorporates an access control system based on blockchain technology16. Many important challenges, such as data security and confidentiality, are raised by digital transformation. The study offered a security architecture that combines smart devices and blockchain technology to offer a secure communication system in an intelligent city17. Greater user ease is brought about by cloud data services, which offer an extendable and convergent method for data sharing amongst different users, reliable cloud services keep and share user data. Many security issues will be raised. Often used in cloud storage systems to address security issues, attribute-based encryption (ABE) is a mathematical method18.
A University of Nicosia (2018) tool makes and stores bitcoin certificates. Additionally, UNIC accepts bitcoin for degree programs. The technique may cost platform users because requires keeping large volumes of data and documents, such as transcripts, diplomas, and certificates19,20,21. The research examines SBTs to overcome the difficulties with the present NFT methodology. Soul bound tokens (Weyl et al., 2022) have been extensively studied and may improve digital document security and verifiability.
Identifying research gaps in the context of a Blockchain framework for ensuring security in healthcare records involves assessing the existing literature and pinpointing areas where further investigation is needed. Below are some potential research gaps in the domain:
-
1.
Integration with Existing Healthcare Systems: Limited studies address the seamless integration of Blockchain solutions with existing healthcare information systems. Further exploration is needed to understand the challenges, strategies, and best practices for integrating Blockchain into diverse healthcare infrastructures.
-
2.
Scalability and Performance Optimization: Existing studies may not adequately address the scalability issues associated. Research is needed to explore scalable solutions and performance optimization techniques to ensure efficient processing and storage. Blockchain technology’s scalability problems are serious obstacles that limit their functionality and wider adoption. These problems are a result of the intrinsic architecture of blockchains, which places a high value on security and decentralization frequently at the expense of scalability.
-
3.
User Acceptance and Usability: Limited attention may have been given to user perspectives, including healthcare professionals, administrators, and patients, regarding the acceptance and usability of Blockchain-based healthcare record systems. More research is needed to understand user concerns, preferences, and barriers to adoption.
-
4.
Interoperability Standards: Interoperability standards for Blockchain-based healthcare systems may not be well-established. Investigating and proposing standardized protocols for data exchange and communication between different healthcare entities using Blockchain technology is a crucial research gap.
-
5.
Regulatory Compliance and Legal Implications: The legal and regulatory aspects of implementing Blockchain in healthcare records need further exploration. Understanding how Blockchain complies with healthcare data protection regulations and addressing legal challenges associated with decentralized systems is an important research area.
-
6.
Privacy-Preserving Techniques: Enhancing privacy in Blockchain-based healthcare records without compromising security is a challenging area. Investigating advanced cryptographic techniques or privacy-preserving protocols specific to healthcare data is essential for filling the gap.
-
7.
Blockchain Consensus Mechanisms in Healthcare: While various Blockchain consensus mechanisms exist, their suitability and effectiveness in healthcare settings may not have been thoroughly studied. Research is needed to evaluate and recommend consensus mechanisms tailored to the requirements and constraints of healthcare data.
-
8.
Cost-Benefit Analysis and ROI: Limited research may have explored the cost-effectiveness and return on investment (ROI) of implementing Blockchain in healthcare records. Investigating the economic viability and long-term benefits of adopting Blockchain is crucial for decision-makers in the healthcare industry.
-
9.
Blockchain Security Threats and Countermeasures: Ongoing advancements in cybersecurity may introduce new threats to Blockchain-based healthcare systems. Research is needed to identify emerging security threats and develop effective countermeasures to protect sensitive healthcare data stored on the Blockchain.
-
10.
Educational Initiatives and Training: empower healthcare professionals with the knowledge and skills required for interacting with Blockchain-based systems Research could explore effective training methods and educational strategies in the context.
-
11.
Utilizing cloud computing to access a decentralized database: Higher Level of Protection: Decentralised databases lessen the possibility of a single point of failure or attack by storing data across several nodes. It is more resistant to cyberattacks and data breaches thanks to its dispersion.
-
12.
Enhanced Accessibility and Dependability: In a decentralized network, high availability is ensured via data redundancy among several nodes. The data is still available from other nodes even in the event of a node failure.
-
13.
Lack of a Single Point of Failure: Decentralised databases increase system reliability by eliminating the possibility of a single point of failure, in contrast to traditional databases that depend on centralized servers.
-
14.
Data privacy and security Aspects: Data security and privacy are major issues when using cloud services and need to be carefully handled. The main elements, difficulties, and recommended procedures for guaranteeing strong data privacy and security in cloud systems are listed below.
Facts regarding data privacy
-
1.
Data Sovereignty and Place of Residence: Problem: The locations for data processing and storage are governed by different national laws.
-
Optimal Method: To ensure compliance with local rules like GDPR in Europe and HIPAA in the US, use cloud providers which offer data centres in different jurisdictions and let you choose the location for your data storage22,23.
-
2.
Minimising Data: Problem: over-collection and storage of data might lead to increased privacy hazards
-
Best Practice: Only gather and keep the data required for your application by data minimization standards. Audit your data storage frequently to get rid of material that is superfluous or out of date.
Data security features
-
1.
Identifying and addressing threats
Problem: Malware, DDoS attacks, and data breaches are just a few of the cyberattacks that can target cloud environments.
Recommendation: Establish thorough methods for detecting and responding to threats, including intrusion detection systems (IDS), security information and event management (SIEM) systems, and routine security audits. Cloud service providers frequently give native security solutions that you can incorporate into your security plan.
-
2.
Data Accuracy
Problem: Maintaining trust requires making sure that data has not been changed or tampered with.
The best practice is to check the integrity of the data using cryptographic hash algorithms. To keep track of data changes and access, use monitoring and logging.
These research gaps provide a foundation for scholars and researchers to contribute valuable insights and advancements in the field of Blockchain for securing healthcare records24.
Motivation and objectives
The study’s main goal is to carry out energy-efficient health monitoring that is fast and secure. A patient’s remote healthcare monitoring system design in WBAN posed several difficulties25. Because is accomplished either intra-WBAN or outside WBAN, current WBAN systems do not provide end-to-end security, low energy consumption, and can create delays. The interference between WBANs occurs when use the same channel at the same time. Periodical data requires the optimum channel for interference-free transmission, while vital data requires an idle channel. High energy usage and end-to-end latency are brought on by single-hop communication for the crucial data. To transmit packets by QoS restrictions, the contention window size (CWS) at the single hop must be modified. None of them gave environmental information about a patient’s health any thought26,27. The following health monitoring-related challenges, of which the principal ones are enumerated below, serve as driving forces.
Particularly in sectors like healthcare, banking, supply chain management, and more, blockchain systems can drastically save costs in several ways.
-
1.
Getting Rid of Middlemen
-
Straight Transactions: Intermediaries like banks, brokers, or clearinghouses are no longer necessary thanks to blockchain technology, which facilitates peer-to-peer transactions. Administrative expenses and transaction fees are decreased.
-
Smart Contracts: Without requiring human interaction, automated smart contracts carry out and uphold agreements, lowering the financial and administrative costs related to contract administration.
-
2.
Increasing Efficiencies
-
Process Automation: Blockchain reduces the time and labour needed for tasks like compliance checks, payments, and settlements by automating and streamlining these operations.
-
Real-Time Data Access: Decentralised ledgers facilitate faster decision-making by offering real-time data access, which also lessens the need for manual audits and reconciliations.
Higher energy consumption: Frequent sensor replacement is necessary when sensors exhaust their energy. Data security and privacy are compromised by wireless channels and the limited energy capacity of sensors. Mobility forecast in a patient is moving around, communications must be secure and energy efficient.
The following list of research goals is included in the paper:
-
To put out a health monitoring system that enables patients to perceive and send data in an energy-efficient manner while still being secure and delay-aware.
-
To maintain QoS restrictions while gathering and sending data from all tiers (intra-WBAN, inter-WBAN, and beyond WBAN).
-
Ensuring the integrity and confidentiality of the data is maintained while securely storing the sensed data on a storage server.
Key elements of blockchain technology
-
Decentralized: Blockchain operates without a central authority, allowing global data recording, storage, and modification without the need for centralized control nodes.
-
Transparent: Trust is established through transparency. All data stored in the blockchain is accessible to every node, ensuring that participants can access the most recent and reliable information.
-
Open Source: Most blockchain systems are public and open source. The transparency enables anyone to review the records and encourages the development of applications by leveraging blockchain technology.
-
Autonomy: Blockchain aims to shift control from individual entities to the entire system. Achieved through consensus mechanisms, ensuring each node on the network can securely transfer or modify data.
-
Immutable: Records in the blockchain are permanent and tamper-proof. The use of cryptographic hashes and the requirement of controlling more than 51% of the nodes simultaneously make extremely difficult to alter recorded information.
Healthcare management
-
Concerns in EHR Management: Despite the benefits of EHRs, concerns persist regarding data ownership and security within these systems.
-
Prominent Blockchain Platforms: Ethereum and Hyperledger are popular choices for implementing blockchain in healthcare. Their permissioned networks and efficient transaction processing make them suitable for managing sensitive health data.
-
Global Initiatives: Governments worldwide recognize the importance of digitizing medical systems. Initiatives like the HITECH Act promote widespread EHR use for societal benefits, emphasizing streamlined administration and enhanced data sharing.
-
Crisis Management and EHRs: Events like the 2019 novel coronavirus outbreak highlight the crucial role of EHRs in crisis management. Blockchain showcases potential in telemonitoring and healthcare technologies during such events.
Cryptographic mechanisms used to create and manage SBTs
To maintain the security, integrity, and non-transferability of Soulbound Tokens (SBTs), several cryptographic techniques are used during the creation and management process.
-
1.
Encryption using Public Keys
-
The objective is to safely link a public key to a person or thing (such a patient or a medical professional).
-
Mechanism: A public key and a private key are the two cryptographic keys that are owned by each individual. Data encryption and digital signature verification are accomplished with the use of the public key, whilst data decryption and digital signature creation are accomplished with the secret key.
-
Usage in SBTs: An address in the wallet that matches the user’s public key receives the SBT. Token ownership and access are limited to the owner of the private key.
-
2.
Hashing Mechanisms
-
The aim is to generate a distinct, fixed-size hash value from an input, such as credentials or medical records.
-
Mechanism: A fixed-length string of bytes is produced using hash functions from an input. Nearly impossible to reverse the process (i.e., generate the input from the output), yet the output is deterministic, meaning the same input will always yield the same output.
-
Utilisation in SBTs: In order to guarantee data integrity and provide speedy confirmation that the data has not been altered, hash functions are utilised to provide distinct IDs for the data kept within the SBT.
-
3.
Proofs Quantum of Knowledge (ZKPs)
-
Goal: To demonstrate understanding of a fact without disclosing the fact itself.
-
Mechanism: Zero-knowledge proofs (ZKPs) let a party demonstrate to another that have their own a value (such a secret key) without divulging any further information.
-
Application in SBTs: ZKPs can be used to improve privacy by verifying claims connected to an SBT (such as medical credentials or treatment history) without disclosing the underlying data.
Benefits and relevance in Soulbound Tokens (SBTs) can greatly improve the Electronic Health Record (EHR) domain
-
1.
Time-limited and reversible effectively in the cloud: To improve data security, privacy, and dynamic access control in cloud-based healthcare systems, a time-controllable approach with effective revocation is proposed for a mobile e-healthcare cloud environment. The method is essential for handling private health information since permits authorized people to view the information for a predetermined amount of time and efficiently revokes access when necessary. For efficiency improvements (e.g., decreasing local storage and processing costs), electronic health (e-health) systems may outsource data, such as patient e-health records, to mobile cloud servers. However, if there are semi-honest cloud servers present, the action might have privacy concerns. While most existing solutions for searchable encryption (SE) do not support temporal access control (i.e., a mechanism that grants access permissions to users for specified time ranges), SE has the potential to enable privacy-preserving searches based on keywords for encrypted data stored in the mobile cloud28. Hence, design a time-controllable keyword search scheme by using an attribute-based comparable access control that allows users to match indexes encrypted at specified time intervals. Then, improves the basic framework to support efficient user revocation using secret sharing. Formally prove the security of our proposed frameworks against chosen-keyword attacks and key collusion attacks, as well as achieving keyword secrecy. It evaluates the performance of our proposed approach using a real-world dataset to demonstrate their practical utility.
-
2.
Effective spatial range protection for privacy: The goal of an effective privacy-preserving spatial range query over outsourced encrypted data is to allow users to conduct secure spatial inquiries (like range searches) on cloud-stored encrypted datasets without disclosing sensitive information about the queries or the data. Applications like healthcare, logistics, and smart city management that require sensitive location-based data benefit greatly from the strategy. Due to the high computational and storage costs associated with the location-based services industry’s rapid growth, many LBS providers are outsourcing spatial data to cloud servers, which raises security risks including location privacy leaks. Large-scale privacy-preserving LBS methods have therefore been put forth. Unfortunately, the current Bloom filter-based methods overlook the redundant bits that do not map information, leading to significant computational overheads, and also fail to expose the Bloom filter’s inclusion relationship29. By expertly combining the Geohash algorithm with the Circular Shift and Coalesce Bloom Filter (CSC-BF) framework and Symmetric-key Hidden Vector Encryption (SHVE), proposes an efficient Privacy-preserving Spatial Range Query (PSRQ) scheme to address these problems. The method significantly lowers the computational cost of generating tokens and improves query efficiency on large-scale datasets. Furthermore, developed a Confused Bloom Filter (CBF) that muddles the inclusion relationship by misinterpreting the Bloom filter’s values of 0 and 1, and added a method PSRQ +. Finally, extensive experimental tests show that our schemes using a million-level dataset improve the query efficiency by 100× compared with previous state-of-the-art solutions, and formal security analysis confirms that our schemes are secure against Indistinguishability under Chosen-Plaintext Attacks (IND-CPA) and PSRQ + achieves adaptive IND-CPA.
Benefits:
-
1.
Strengthened Identity Confirmation: SBTs offer a reliable and unchangeable method of credential and identity verification.
-
2.
SBTs provide a safe and impenetrable method for storing private health data.
-
3.
SBTs can enable smooth information exchange between various healthcare providers and systems.
Relevance:
-
Patient Identity: SBTs can guarantee precise patient identity among various healthcare providers, minimizing the occurrence of misidentification and guaranteeing that medical records are appropriately matched to the appropriate parties.
-
Data Integrity: SBTs provide the security and dependability of patient data by making health records impossible to change or tamper with.
-
Cross-Institutional Data Sharing: SBTs can make possible for various healthcare facilities to safely and effectively exchange patient data, enhancing care coordination and lowering the possibility of medical mistakes.
Using soulbound tokens and pseudo code, medical document verification on the blockchain
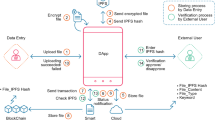
Start: SBT_enabled_hospital (Step 1)
Start the blockchain from scratch and make a fresh soulbound token contract.
-
2.
Confirm which hospitals are authorized to provide SBTs.
-
3.
Establish a user interface so that papers may be uploaded and verified.
-
4.
Figure 2 shows the logic of verification of institutions allowed to mint SBTs as below.
SBT_Enabled_document in Step 2
Section A: Process of uploading documents:
Digital document input.
Result: Soulbound token Method:
-
1.
The document is uploaded to the interface by the hospital.
-
2.
The document is hashed and placed as a soulbound token on the blockchain.
-
3.
The user’s identity is connected to the soulbound token.
In Fig. 3, the patients at the accredited hospitals and facilities may receive fresh SBTs. These SBTs include the URL for the document’s decentralized network hosting—which takes the form of a prescription or report.
Part B:
To create a digital medical record.
Input soulbound tokens.
Output: Soulbound token hash.
-
Step 1: Access the user’s address and obtain a medical record.
-
2. Users’ soulbound token ownership is validated.
-
3. The soulbound tokens are hashed using the SHA256 technique after verification.
Figure 4 demonstrates the phase of generation of a hash of soulbound tokens on IPFS.
Step 3: Document verification with SBT enabled
Enter: URL of digital health record Output: Verified or unverified document Method:
-
1.
The user authenticates himself to the verification system by presenting their medical record.
-
2.
The soulbound tokens connected to the displayed record are retrieved by the system.
-
3.
The system verifies the connection between the user’s identity and the soulbound token.
-
4.
The document is validated, and the verification is noted on the blockchain if the connection is legitimate.
-
5.
The verification request is denied if the link is not legitimate.
In Fig. 5, Using blockchain technology, cryptographic concepts, and smart contracts, create a system that ensures secure, verifiable, and non-transferable medical records by automating record authentication using Soulbound Tokens (SBTs), the digital medical record can be verified by utilizing the hospital’s token ID and smart contract address to get the owner of the SBTs included in the record from the blockchain.
Connecting SBTs to health records
-
1.
The issuing of SBTs:
-
Enrollment of Patients: A patient receives an SBT from the healthcare practitioner at the time of registration in a healthcare system. The patient’s digital wallet houses the SBT30,31.
-
Metadata and Identifiable Labels: Together with a unique identity (hash) that matches the patient’s medical records, the SBT also contains metadata about the patient and the issuer, such as hospital details.
-
2.
The issuing of SBTs:
-
Making of Records: A healthcare professional enters or modifies a patient’s medical history in the electronic health record (EHR) system during an appointment.
-
Hash Production: a cryptographic hash function is used to hash the medical record. Through the process, the record is transformed into a fixed-length character string that is specific to contents. A slight alteration in the record would provide an entirely distinct hash.
Guaranteeing the genuineness of health records
Electronic Signatures:
-
1.
Sealing Documents: A healthcare professional uses their private key to sign medical records that t produces or amend. The digital signature attests to the document’s creation or approval from a reliable source.
-
2.
Validation: Verifying the signature ensures that the record has not been altered and establishes the signer’s identity for anyone who has access to the public key of the provider25,32.
Unchangeability of blockchain
Mutation-Proof Documents: The medical record’s hash cannot be changed after is stored on the blockchain; only the hash can be updated. Any attempt to alter the recorded hash would be obvious because the blockchain itself is unchangeable. Verified that the patient’s address matches the SBT owner’s after gaining access to the SBT owner. The SBTs are validated if the owners are the same shown in Fig. 6 as below.
Limitations related to SBT-based authentication
Issues with non-transferability:
-
Lack of adaptability: Problem: Since SBTs aren’t portable by nature, patients may find themselves in a situation where need to switch digital wallets because of theft, loss, or other circumstances.
Crucial Management Concerns:
-
Loss of Private Keys: Secure private key management is required for both patients and healthcare professionals. The SBT and related medical records are inaccessible in the event of a lost private key.
-
Repercussions: Losing a key can result in irreversible access to vital medical data, which puts patient care at serious risk.
Challenges related to SBT-based authentication
Technological difficulties
-
Cooperation: Different blockchain platforms and traditional databases may be used by healthcare systems. Ensuring these disparate systems work together is difficult yet necessary for smooth data integration and sharing33,34.
-
Information Storage: Direct storage of massive amounts of data is not a good fit for blockchain technology. Dependability and security of off-chain storage solutions are required because only hashes or references to medical records can be stored on-chain, adding to the complexity.
Limitations and challenges on scalability, restrictions on resources, lack of standards, regulatory requirements, and user adoption barriers
-
Scalability: Scaling, controlling, and maintaining infrastructure becomes increasingly difficult as systems get larger. However, covers both operational and technical complexity, such as making sure databases, networks, and applications can handle increased demands.
-
Restriction of Resources: Limitations in terms of computational power, storage, or bandwidth may be physical or cloud-based, and can become expensive or challenging to maintain on a big scale.
-
architectural limitations Not all architectural designs are intended to scale well; for example, microservices scale more easily than monolithic systems.
-
Lack of standards: Interoperability Issues: The inability of disparate systems or technologies to cooperate arises from the lack of industry standards.
-
Fragmentation: Different approaches to the same problem can result in ecosystems that are divided into parts because of the incompatibilities between the solutions.
-
The cost and duration of development are increased when there is no single set of standards and developers must create their solutions or adjust to different ones.
-
Security Risks: Inconsistent security protocols could result from the absence of standards, which could expose vulnerabilities.
-
Regulatory requirements: Costs associated with compliance: Adhering to rules can be expensive, particularly when scaling across several regions with disparate laws (such as the CCPA in California and the GDPR in Europe). Organizations might have to put in place particular security, privacy, and auditing procedures.
-
Data Governance: Tight guidelines for the transfer, storage, and use of data can restrict the flexibility of operations, particularly in companies that rely heavily on data.
-
Legal Risks: Violations of regulations may result in severe fines and harm to one’s image. For innovators, legal frameworks frequently lag behind technological developments.
-
Geographical Restrictions: The deployment of global systems may be hampered by regulatory constraints that impose geographic restrictions (such as data localization regulations).
-
User adoption barriers: Learning Curve: Users may be slow to adopt new technologies due to steep learning curves, fear of change, or unfamiliarity with new systems. Lack of Trust: Trust issues, particularly related to security, privacy, or transparency, can deter users from adopting a system. Cultural Resistance: In some cases, users may resist changes due to cultural or organizational inertia, where established practices are deeply ingrained. Poor User Experience (UX): If a product or service is difficult to use, even technologically superior solutions may face adoption challenges. Cost and Accessibility: High costs or lack of accessibility can also pose significant barriers to adoption, particularly in developing regions or among lower-income user segments.
Methodology/ system model
The blockchain-based soulbound token system for credential issuance, verification, and recovery is suggested as a solution. With selective disclosure, the system gives users total control over credential information.
-
Gas fees: On blockchain networks such as Ethereum, gas fees are payments made by users to offset the computational energy used to process and verify transactions35,36.
-
Transaction costs: The expenses incurred when moving assets or carrying out transactions on a blockchain network are referred to as transaction costs. These can cover more extensive cost schemes on several platforms in addition to petrol fees.
-
Maintenance overhead: The continuing expenditures of running and maintaining blockchain infrastructure, such as those related to software, hardware, and labour, are referred to as maintenance overhead37.
The credentials are distributed in the form of NFT on the blockchain, and the NFT data is encrypted and saved on the IPFS (Interplanetary File System). Ensuring efficiency, dependability, and security in a dispersed network requires optimising asset distribution38, 39. Several tactics and procedures, like as load balancing, decentralised ledger technology, and efficient data storage and access, are used in the process. These are all customized to the unique needs of the network and the characteristics of the assets.
System model
Three entities are involved in the implementation of the suggested solution: the issuer entity, the verifier, and the user (holder). The agency that oversees and distributes the SBT to the user may be any reputable agency or government division. The user is a regular person who contacts the organization to request the issuance of credentials. People or organizations seeking to verify credentials can act as the verifier. The credential issuance and recovery process’s system architecture are shown in Fig. 7 as follows:
Figure 7 depicts a user registration to register with the system providing the necessary information and the system verifies the information and creates a user profile. In credential Issuance, the system generates a unique credential (e.g. username/password, token, certificate).
Deploying contract
The SBT contract is published by the issuing organization on the blockchain, which is accessible by any business.
Complexity and challenges
-
1.
Integration with present Systems: Considerable infrastructure changes are necessary in order to integrate SBTs with the present EHR systems. EHR systems are frequently complicated and proprietary, which makes integration difficult40.
-
2.
Blockchain Technology: Setting up and managing blockchain infrastructure is necessary for implementing SBTs. The calls for knowledge of blockchain technology, which can be expensive.
Advantages and disadvantages
-
1.
The risk of impersonation, identity theft, and illegal access is reduced when credentials are issued through a secure mechanism that guarantees only authorized users receive them.
-
2.
If users misplace or forget their credentials, modern credential systems with user-friendly recovery methods (such as self-service password resets, recovery codes, or backup emails) give them flexibility41.
-
3.
Users may be vulnerable to brute-force, social engineering, or phishing attacks due to inadequate credential issuing or recovery procedures. Particularly vulnerable are poorly designed password recovery mechanisms, including readily guessed security questions.
Challenges:
-
1.
Scalability: When handling many transactions, blockchain networks may encounter scalability problems. Essential to make sure the system can manage the data load of a complete healthcare system.
Scalability concerns:
Throughput of Transactions
-
Problem: Compared to centralized databases, decentralized databases, those built on blockchains often have poorer transaction throughput. If a large number of transactions are processed, may cause bottlenecks.
-
Solution: To increase throughput, implement layer-2 scaling techniques like state channels, rollups, or sidechains to offload transactions from the main chain.
Time lag:
-
Problem: Real-time data processing might be difficult in decentralized networks due to delays caused by the time takes for consensus to be reached.
-
Solution: To cut down on delay, use consensus techniques like Proof-of-Stake (PoS) or Practical Byzantine Fault Tolerance (PBFT), which provide faster finality.
Potential trade-offs:
-
1.
Decentralization versus effectiveness
Trade-off: More nodes and a more intricate consensus process are usually associated with higher levels of decentralisation, which can reduce speed and increase latency. Strike a balance by implementing hybrid models that use a public blockchain for ultimate settlement and transparency but handle important data and transactions on a more centralised layer (such as a private or consortium blockchain).
-
2.
Safety versus Expandability:
-
Trade-off: By using sidechains or sharding to increase scalability, new attack avenues and security flaws may be introduced.
-
Balance: Build sidechains and sharding systems with strong security protocols and audit the system frequently to find and remove vulnerabilities.
-
3.
Interoperability: Standardised protocols and interfaces are necessary to achieve interoperability between various blockchain networks and conventional EHR systems, which might be challenging to achieve.
Issuing of credential
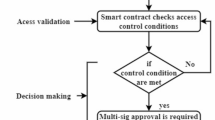
The request to issue the credential is made by the user. The user provides the organization with their identity, wallet address, and guardians’ address. The company then confirms the user identity data and looks up legitimate guardian addresses, which can’t be repeated. The organization executes the issueCredential () method on the SBT contract when the data has been satisfactorily verified. These are the stages that the issueCredential() method takes to operate.
Credential characteristics are generated via the off-chain function and encrypted using the user’s public key. The off-chain function creates the encrypted credential and uploads to IPFS depicted in Figs. 8, 9 and 10.
In Fig. 8. Representation of the soulbound token where to design the program flow for issuing the soul-bound token credential to both the user and the organization. The user registers with the system, providing necessary information (e.g. name, email, organization). In organization registration, the organization registers with the system, providing necessary information (e.g. name, contact, information, etc.)
Figure 9 shows selective credential disclosure allows users to share only the necessary information from their credentials with different verifiers, maintaining privacy and security. In user requests verification, the verifier requests credentials, user selects credentials and verifier credentials.
Figure 10 shows user requests verification where the user initiates a request to verify their soul-bound token credential with a verifier. The verifier requests the user to present their soul-bound token credential.
Verification of credentials
The method selectively discloses credentials to the verifier. The credential holder decides what to show the verifier. Figure 3 shows selective credential sharing to several verifiers. The verifier requests the holder’s SBT credential to commence verification. Unlocked with their private key, and then can read. Holders can divulge attributes to verifiers only. Holder decrypts credential properties with private key. The holder encrypts with the verifier’s public key and sends to them. Verifiers decrypt holder data. The holder verifier verifies credential authenticity in Fig. 4.
Recovery process for SBT
The user enters the new wallet address when calling reissueCredential(). Guardians must retrieve credentials using SBT contract’s initiateRecovery() function. If the function is invoked more than the minimal number of times, executeRecovery() is called. The old SBT will be burnt and the new SBT issued to the new user wallet address in Fig. 11.
For Fig. 11. Improved data integrity, access control, and interoperability, Soulbound Tokens (SBTs) integration can be integrated with Electronic Health Records (EHR) security.
Strengthened identity confirmation
Application:
Individual patient identifiers: Every patient receives a distinct SBT that is securely connected to their EHR. health records are guaranteed to be accurately linked to the appropriate person.
Unchangeable credentials: Healthcare organisations and providers can designate SBTs as a representation of their licences and credentials, guaranteeing that only validated organisations are able to view or alter EHRs.
Advantages of Security:
Stops Identity Theft: SBTs offer a tamper-proof way to confirm the identities of patients and providers, lowering the possibility of identity theft.
Immutable Record: SBTs are unchangeable once are issued, guaranteeing the validity and consistency of patient identification numbers and credentials.
Figure 12 shows a generalized program flow for reissuing a “soul-bound token credential” between a user and an organization. User request re-issuance which the user initiates a request to reissue their soul-bound token credential. The request can be made through a user interface or an API. The organization verifies the request, revocation of previous credentials, binding new credentials, and delivery of new credentials.
Smart contract
One smart contract credential (SBT) is used in the scheme. Solidity is the language used in the smart contract. Once the organization verifies the user identification off-chain, the function initiateCredentialRequest () is executed. The accepts as input an array of guardian addresses and the user address. The addresses that wish to take on the role of guardian for the user address are known as guardian addresses. The function runs the issueCredential () function after verifying that guardian addresses are legitimate.
The guardian addresses hash is added to the appropriate mapping with the user address by addGuardian() function, which accepts as inputs the user address and their corresponding guardian addresses array. The looks for guardian address duplication before adding to the mapping. The user address was entered into the issueCredential() method, which used to issue the SBT credential to the user address. Multiple function calls are used by function. starts by using the getCredentialUrl() function, which uses a chain-link oracle to search the organization’s private database for the credential and connect to an off-chain API. Using the user’s public key, API encrypts the credential characteristics before uploading them to the IPFS. The issueCredential() function receives the produced file URL back. Invokes the safeMintCredential() method to mint the soulbound token for the token URL and assign it to the use address after receiving the credential file URL from the function. Finally, stores the tokenId in the addressToSBT mapping associated with that user address shown in Fig. 13.
Revoke() deletes the user’s tokenId. Reissuing the SBT via the recovery method activates the function. The initiate recovery() function lets a guardian start user recovery.
Performance analysis
The method of assessing the suggested algorithm’s efficacy and efficiency is investigated. Examining the suggested system and comparing total man-hours spent verifying to the available manual approaches, it is established how differs from them. To assess the overall effectiveness of the suggested system, several measuring criteria are used, including the amount of time required for verification, spending, authentication, security, and automation.
Time
The intricacy can all have a significant impact on how long takes to verify a medical document42. A medical document’s complete verification generally takes a few days to several weeks. The reading data stored by SBT from a blockchain can be done rather quickly. In Polygon, adding a block typically takes 2.2 s on average.
Security and authentication
The following are some of the reasons that make having SBTs for medical records unnecessary43:
-
Immutability: Data cannot be changed or removed from a blockchain once has been recorded there, making more difficult for someone to alter the data or create false records or documents.
-
Decentralization: Because blockchains are dispersed among several computers, or nodes are decentralized, making difficult for one person to manage the data or make changes to without the network’s consent.
-
Cryptographic hashing: By putting some data through a mathematical procedure, cryptographic hashing creates a distinct “hash” that serves as a representation of the original material. Without disclosing the actual substance of the data, hash can be used to confirm their legitimacy.
-
Consensus algorithms: Before a transaction is put to the blockchain using these techniques, several nodes on the network must agree on its validity.
Automation
Prescriptions, reports, and other medical records need to be verified. The is a laborious process that is not automated at the moment. Prior to validating a particular document, the patient must first be validated using their social security number, medical record number, allocated identification number, etc. A patient who possesses soulbound tokens can use them to build a hash of other soulbound tokens45. All the information on the patient’s prescriptions and medical reports is contained in the hash. By providing the hospital or institution with one hash, which includes information about all the patient’s soulbound tokens.
Security analysis
While integrating Soulbound Tokens (SBTs) into current healthcare systems, a thorough security study that ensures the system’s security and dependability must be provided. The entails addressing several security tiers, and putting in place strong controls.
Issues with Blockchain Security Resolved:
-
51% Attack: The probability of a 51% attack is decreased by implementing Proof of Stake (PoS) or a permissioned blockchain in which validators are pre-selected based on reputation and trust. Smart Contract Bugs: To guarantee that the code is safe and secure, comprehensive audits and formal verification techniques are used.
-
Assurances: Robust Consensus Mechanisms: By utilizing permissioned blockchain models and proof-of-work techniques, the likelihood of a 51% attack is reduced, guaranteeing the blockchain’s integrity. validated Smart Contracts: Formally validated and audited smart contracts ensure that the tokens are secure and effective.
-
Access Control: A multi-domain security analysis emphasizes access control and concentrates on vulnerabilities that extend beyond blockchain technology. Information security relies heavily on access control, which establishes the conditions and individuals permitted to view data or resources.
-
Authentication: A security analysis that looks beyond blockchain to identify authentication concerns covers a variety of potential dangers that can occur in both conventional and contemporary digital contexts. An essential security measure is authentication, which is used to confirm a user’s, device’s, or system’s identity before allowing access to resources.
-
Encryption: A security analysis that goes beyond blockchain technology to address encryption-related dangers covers several important domains where encryption, while essential to data security, can present own set of difficulties. Encryption is essential for protecting the confidentiality and integrity of data, but it is not implemented or managed properly, systems may become vulnerable.
-
Patient Privacy: The issues of safeguarding sensitive health information (PHI) and guaranteeing adherence to privacy rules such as HIPAA (Health Insurance Portability and Accountability Act) are addressed by a security analysis that centers on patient privacy. Protecting sensitive data, preventing breaches, and guaranteeing the privacy, availability, and integrity of medical information are all part of patient data security, which goes beyond conventional cybersecurity procedures.
The proposed system offers some performance advantages, particularly in data access speed, while maintaining strong security features. However, there are some trade-offs:
-
Transaction throughput: The document doesn’t provide specific throughput numbers but mentions that the system takes about 5 s longer to process 50 queries compared to a system without authentication. This suggests a moderate impact on throughput.
-
Latency: The blockchain-based IPFS storage shows lower latency in data access compared to centralized S3 storage. This is a significant advantage for the proposed system.
-
Resource utilization: While not directly measured, the use of blockchain and IPFS suggests a more distributed resource utilization compared to centralized approaches. This could potentially lead to better scalability and resilience.
-
Security vs. Performance trade-off: The IKGSR encryption algorithm used in the proposed system takes longer for encryption and decryption compared to traditional RSA, but offers enhanced security features.
Table 1 resume the Comparison from Blockchain-Based Framework for Interoperable Electronic Health Records for an Improved Healthcare System.
Results
Soulbound tokens may be able to offer a tamper-proof record of a document’s legitimacy in the context of document verification. Rise to an unchangeable and safe record of the document’s issuance that anybody with blockchain access could confirm shown in Figs. 14, 15, 16 and 17.
Figure 14 shows the representation of document verification can vary depending on the context and the specific requirements of the system (document submission, document validation, data extraction, verification, decision, notification and their record keeping).
Consent management in clinical trials using smart contracts
A proof-of-concept system for managing patient consent in clinical trials was created utilizing distributed ledger technologies and smart contracts46. By using encryption, the intention was to preserve patient privacy while guaranteeing responsibility and openness in the handling of consent. A clinical trial setting with actual patient data was used to test the prototype. The blockchain ensured that every transaction was safely recorded, and users could provide or withdraw approval in real-time. Identities of patients were secured during data gathering using encryption. The prototype was successful in guaranteeing that patient permission was securely recorded and confirmed in an unchangeable manner. Consent could be withdrawn by patients at any time, and study administrators were alerted right away. The prototype’s performance provides evidence that blockchain and encryption technologies have the potential to improve clinical trial consent management and foster more patient-provider trust.
The following possible effects:
-
1.
Enhanced authentication: Soulbound tokens offer a safe, unchangeable record of a document’s validity, which can help lower the possibility of fraud and counterfeiting.
Figure 15 shows enhanced authentication and involves authentication factors (Knowledge factor, possession factor, biometric factor), authentication request where the system sends a request to the user to provide the additional authentication factors based on the chosen methods.
-
2.
Enhanced efficiency: Hospitals can expedite their document verification procedures by employing soulbound tokens, as the blockchain facilitates the rapid and simple authentication of a document’s legitimacy.
Figure 16 shows the enhanced efficiency of a system where process optimization, automation, resource allocation, performance monitoring, training and development, and collaboration and communication.
-
3.
Greater transparency: Soulbound tokens can boost trust in the document verification process by enabling everyone with blockchain access to confirm a document’s legitimacy.
Figure 17 shows information accessibility, open communication, data sharing, decision-making process, accountability, compliance, and regulations.
-
4.
Improved interoperability: Soulbound tokens can be used to establish a medical record verification standard that works with many systems and organizations, making easier to share and use digital data.
Completing the interoperability strategy needed to integrate Soulbound Tokens (SBTs) with current healthcare systems is imperative. To guarantee a smooth and safe integration, the approach should take organizational, technical, and regulatory factors into consideration.
Figure 18 shows improved interoperability in a system where data exchange, system integration, cross-platform compatibility, APIs and Interfaces, Data mapping and transformation, and Semantic Interoperability.
Context of simulation
Table 2 Shows the simulation setting of the proposed blockchain-based Soulbound Token (SBT) system essential parameters and mechanisms used in the simulation. Figure 19 shows the number of hashes needed to establish a selective disclosure credential. Simple public cryptography strategy is compared to the merkle tree selective disclosure method in the paper. The number of hashes needed to confirm selective disclosure credentials is shown in Fig. 20. The method has constant time, unlike the merkle tree approach, which takes log(N).
Conclusion
Medical document verification is an important yet expensive process that usually depends on centralized databases, which causes inefficiencies because of human validation techniques. By boosting efficiency, decreasing fraud, and strengthening security, the application of blockchain technology presents a possible answer to these problems. The paper offers a blockchain-based system that uses SBTs to automatically authenticate and verify records, resulting in the creation of an immutable, decentralized credential system associated with these data. The suggested system offers quick access to a decentralized database and drastically cuts down on verification time by integrating cloud computing. Additionally, by improving the most efficient distribution of resources throughout a dispersed network, the blockchain system’s integration of deep learning algorithms lowers platform expenses. When using blockchain, SBTs, and cloud computing, there are clear advantages in terms of less fraud and better efficiency. In addition to ensuring the availability and integrity of decentralized databases, the system speeds up the verification procedure. Future studies may examine the system’s scalability and possible uses in other areas, opening the door to more effective and safe document verification procedures in a variety of fields.
Data availability
The datasets used during the current work are available from the corresponding author on reasonable request.
References
Villarreal, E. R. D., García-Alonso, J., Moguel, E. & Alegría, J. A. H. Blockchain for healthcare management systems: A survey on interoperability and security. IEEE Access11, 5629–5652 (2023).
Khan, Abdullah Ayub, Sami Bourouis, M. M. Kamruzzaman, Myriam Hadjouni, Zaffar Ahmed Shaikh, Asif Ali Laghari, Hela Elmannai, and Sami Dhahbi. Data security in healthcare industrial internet of things with blockchain. IEEE Sensors J.2(20), 21544-25151 (2023).https://doi.org/10.1109/JSEN.2023.3273851.
Abdullah Ayub Khan, Xuzhuo Zhang, Fahima Hajjej, Jing Yang, Chin Soon Ku, Lip Yee Por, ASMF: Ambient social media forensics chain of custody with an intelligent digital investigation process using federated learning, Heliyon,10(1)(2024). https://doi.org/10.1016/j.heliyon.2023.e23254.
Khan AA, et al. GAN-IoTVS: A Novel Internet of Multimedia Things-enabled Video Streaming Compression Model Using GAN and Fuzzy Logic. IEEE Sensors J.23(23), 29434-29441 (2023). https://doi.org/10.1109/JSEN.2023.3316088.
Ayub Khan A, Laghari AA, M. Baqasah A, Alroobaea R, Almadhor A, Avelino Sampedro G, Kryvinska N. 2024. Blockchain-enabled infrastructural security solution for serverless consortium fog and edge computing. PeerJ Computer Science. https://doi.org/10.7717/peerj-cs.1933.
Khan, A. A. VI. et al. Artificial intelligence and blockchain technology for secure smart grid and power distribution Automation: A State-of-the-Art Review. Sustainable Energy Tech Asses57, 103282 (2023).
Singh, P. & Verma, S. Analysis on Different Strategies Used in Blockchain Technology. J Comput Theor Nanosci16(10), 4350–4355 (2019).
Araujo-Inastrilla C. R., Vitón-Castillo A. A. Blockchain in health sciences: Research trends in Scopus. Iberoam J Sci Meas Commun. 3 (2) (2023). https://doi.org/10.47909/ijsmc.56.
Lakhan, A. et al. DRLBTS: deep reinforcement learning-aware blockchain-based healthcare system. Sci Rep13(1), 4124 (2023).
Ahmad, S., Arya, S. K., Gupta, S., Singh, P., & Dwivedi, S. K. Study of Cryptographic Techniques Adopted in Blockchain. In 2023 4th International Conference on Intelligent Engineering and Management (ICIEM). pp. 1–6. (IEEE, 2023). https://doi.org/10.1109/ICIEM59379.2023.10166591.
Kaushik, K. & Kumar, A. Demystifying quantum blockchain for healthcare. Sec Privacy6(3), e284 (2023).
Sun, M., Chai, Q., & Ng, C. T. Managing the quality-speed tradeoff in blockchain-supported healthcare diagnostic services. Omega. 120, 102911 (2023). https://doi.org/10.1016/j.omega.2023.102911.
Tareen, F. N. et al. Efficient Load Balancing for Blockchain-Based Healthcare System in Smart Cities. Appl Sci13(4), 2411 (2023).
Bennacer, S. A., Sabiri, K., Aaroud, A., Akodadi, K. & Cherradi, B. A comprehensive survey on blockchain-based healthcare industry: Applications and challenges. Indones. J. Electr. Eng. Comput. Sci30, 1558–1571 (2023).
Singh, P., Singh, A. and Gupta, A. Design Strategies for Mobile Ad-hoc Network to Prevent from Attack. In Proceedings of the 3rd International Conference on Advanced Computing and Software Engineering (ICACSE 2021), 194-201. https://doi.org/10.5220/0010566800003161 .
Chinnasamy, P., Vinodhini, B., Praveena, V., Vinothini, C., & Sujitha, B. B. Blockchain based access control and data sharing systems for smart devices. Journal of Physics: Conference Series (Vol. 1767, No. 1, p. 012056). International E- Conference on Data Analytics, Intelligent Systems and Information Security & ICDIIS 2020 11-12 December 2020. (Pollachi, IOP Publishing, 2021). httsps://https://doi.org/10.1088/1742-6596/1767/1/012056.
Chinnasamy, P. et al. Blockchain technology in smart-cities. In Blockchain technology: Applications and challenges 179–200 (Springer International Publishing, Cham, 2021).
Chinnasamy, P., Praveena, V. Secure and Efficient Data Sharing Scheme in Cloud for Protecting Data in Smart Cities. In: Al-Turjman, F., Gowthaman, N. (eds) Advanced Controllers for Smart Cities. EAI/Springer Innovations in Communication and Computing. Springer, Cham. (2021). https://doi.org/10.1007/978-3-030-48539-9_4.
Aloini, D., Benevento, E., Stefanini, A. & Zerbino, P. Transforming healthcare ecosystems through blockchain: Opportunities and capabilities for business process innovation. Technovation119, 102557 (2023).
Hajian, A., Prybutok, V. R. & Chang, H. C. An empirical study for blockchain-based information sharing systems in electronic health records: A mediation perspective. Comput Human Behav138, 107471 (2023).
Hegde, P. & Maddikunta, P. K. R. Secure PBFT Consensus-Based Lightweight Blockchain for Healthcare Application. Appl Sci13(6), 3757 (2023).
Wenhua, Z. et al. Blockchain technology: security issues, healthcare applications, challenges and future trends. Electronics12(3), 546 (2023).
Singh, P., Sinha, P., & Raghav, A. A Blockchain IoT Hybrid Framework for Security and Privacy in a Healthcare Database Network. In Dynamics of Swarm Intelligence Health Analysis for the Next Generation. pp. 210–225. (IGI Global, 2023). https://doi.org/10.4018/978-1-6684-6894-4.ch011.
Sharma, P., Namasudra, S., Crespo, R. G., Parra-Fuente, J. & Trivedi, M. C. EHDHE: Enhancing security of healthcare documents in IoT-enabled digital healthcare ecosystems using blockchain. Inf Sci629, 703–718 (2023).
Sinha, P., Singh, R., Roy, R., & Singh, P. Education and Analysis of Autistic Patients Using Machine Learning. In 2022 International Conference on Emerging Smart Computing and Informatics (ESCI). pp. 1–6. (IEEE, 2022). https://doi.org/10.1109/ESCI53509.2022.9758322.
Ali, A., Al-Rimy, B. A. S., Alsubaei, F. S., Almazroi, A. A. & Almazroi, A. A. HealthLock: Blockchain-Based Privacy Preservation Using Homomorphic Encryption in Internet of Things Healthcare Applications. Sensors23(15), 6762 (2023).
Badri, S., Ullah, Jan S., Alghazzawi, D., Aldhaheri, S. & Pitropakis, N. BIoMT: A Blockchain-Enabled Healthcare Architecture for Information Security in the Internet of Medical Things (2023).
Miao, Y. et al. Time-controllable keyword search scheme with efficient revocation in mobile e-health cloud. IEEE Transact Mobile Comput23(5), 3650–3665 (2023).
Miao, Y. et al. Efficient privacy-preserving spatial range query over outsourced encrypted data. IEEE Transact Inform Forensics Sec18, 3921–3933 (2023).
Kiania, K., Jameii, S.M. & Rahmani, A.M. Blockchain-based privacy and security preserving in electronic health: a systematic review. Multimed Tools Appl 82, 28493–28519 (2023). https://doi.org/10.1007/s11042-023-14488-w
Miriam, H., Doreen, D., Dahiya, D., & Rene Robin, C. R. Secured Cyber Security Algorithm for Healthcare System Using Blockchain Technology. Intell Automation Soft Comput. 35 (2), 1889-1906(2023). https://doi.org/10.32604/iasc.2023.028850.
Singh, P., Sinha, P., & Raghav, A. A Blockchain IoT Hybrid Framework for Security and Privacy in a Healthcare Database Network. In Dynamics of Swarm Intelligence Health Analysis for the Next Generation. pp. 210–225. (IGI Global, 2023). 10.4018/978-1-6684-6894-4.ch011.
Pathak, R., Soni, B. & Muppalaneni, N. B. Role of Blockchain in Health Care: A Comprehensive Study. In Proceedings of 3rd International Conference on Recent Trends in Machine Learning, IoT, Smart Cities and Applications: ICMISC 2022 137–154 (Springer Nature Singapore, Singapore, 2023).
Elgamal, E., Medhat, W., Abd Elfatah, M., & Abdelbaki, N. Blockchain in Healthcare for Achieving Patients’ Privacy. In 2023 20th Learning and Technology Conference (L&T). pp. 59–64. (IEEE, 2023). 10.1109/LT58159.2023.10092352.
Pradhan, N., Sagar, S. & Jagadesh, T. Advance Convolutional Network Architecture for MRI Data Investigation for Alzheimer’s Disease Early Diagnosis. SN Comput Sci5(1), 167 (2024).
Pradhan, N., Sagar, S. & Singh, A. S. Analysis of MRI image data for Alzheimer disease detection using deep learning techniques. Multimedia Tools Appl83(6), 17729–17752 (2024).
Khaitan, S., Sagar, S. & Agarwal, R. Chaos cryptosystem with optimal key selection for image encryption. Multimedia Tools Appl82(25), 39653–39668 (2023).
Khan, A. A. et al. Healthcare ledger management: A blockchain and machine learning-enabled novel and secure architecture for medical industry. Hum Cent Comput Inf Sci.12, 55 (2022).
Singh, P. & Sagar, S. Towards Trustworthy Healthcare Systems: Designing Blockchain-Based Secure Electronic Health Records. Int J Comput Digital Syst17(1), 1–28 (2024).
David, S., Duraipandian, K., Chandrasekaran, D., Pandey, D., Sindhwani, N., & Pandey, B. Chapter 3 - Impact of blockchain in healthcare system, Editor(s): Mangesh M. Ghonge, Pradeep N., Amar Das, Yulei Wu, Om Pal, Unleashing the Potentials of Blockchain Technology for Healthcare Industries, Academic Press. 37-57, ISBN 9780323994811 (2023). https://doi.org/10.1016/B978-0-323-99481-1.00004-3.
Vishwakarma, A., Dangayach, G. S., Meena, M. L., Gupta, S. & Luthra, S. Adoption of blockchain technology enabled healthcare sustainable supply chain to improve healthcare supply chain performance. Manag Environ Qual Int J34(4), 1111–1128 (2023).
Karmakar, A., Ghosh, P., Banerjee, P. S. & De, D. ChainSure: Agent free insurance system using blockchain for healthcare 4.0. Intell Syst Appl17, 200177 (2023).
Singh, P., & Sagar, S. Transaction Delay Of Data Transmission Between Sensor And Blockchain Technology For The Healthcare Domain Using Consensus Mechanism. Russian Law J.11 (13s), 322-332 (2023).
Singh, P. & Sagar, S. Healthcare monitoring system with blockchain technology encompassing energy harvesting and delays in a Wideband Network. J Integr Sci Technol12(4), 794–794 (2024).
Bhadoria, R., Singh, P., & Ahmad, S. A Comprehensive Study of Blockchain Technology Trends and Analysis in the Healthcare Industry 4.0. In International Conference on Recent Developments in Cyber Security. (pp. 567–581). (Springer Nature Singapore, Singapore, 2023).
Chinnasamy, P. et al. Smart contract-enabled secure sharing of health data for a mobile cloud-based e-health system. Appl Sci13(6), 3970 (2023).
Acknowledgements
This research was financially supported by Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2024R237), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Funding
The research was financially supported by Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2024R237), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Author information
Authors and Affiliations
Contributions
All authors contributed equally to the conceptualization, formal analysis, investigation, methodology, and writing and editing of the original draft. All authors have read and agreed to the published version of the manuscript.
Corresponding author
Ethics declarations
Ethics approval and consent to participate
Not applicable.
Consent for publication
Not applicable.
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/.
About this article
Cite this article
Singh, P., Sagar, S., Singh, S. et al. Blockchain-enabled verification of medical records using soul-bound tokens and cloud computing. Sci Rep 14, 24830 (2024). https://doi.org/10.1038/s41598-024-75708-3
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-024-75708-3