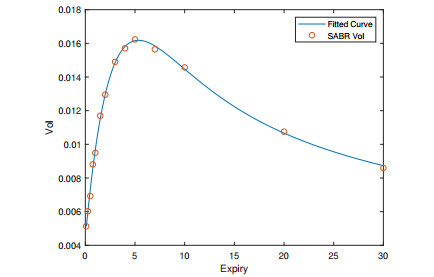
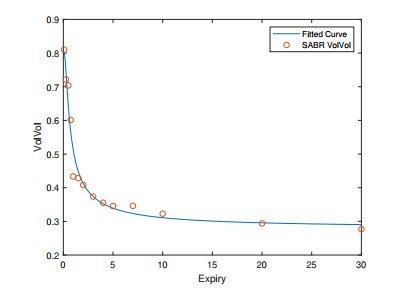
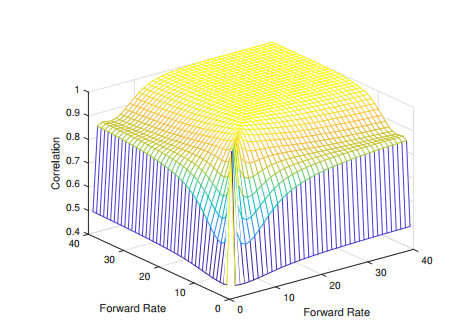
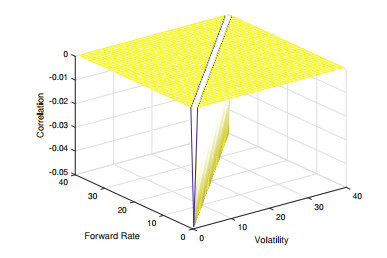
Variations of Libor Market Model (LMM), including Constant Elasticity of Variance-LMM (CEV-LMM) and Stochastic Alpha-Beta-Rho LMM (SABR-LMM), have become popular for modeling interest rate term structure. Nevertheless, the limitation of applying CEV-/SABR-LMM to model negative interest rates still exists. In this paper, we adopt the approach of Free-Boundary SABR (FB-SABR), which is an extension based on standard SABR. The key idea of FB-SABR is to apply absolute value of forward rate |Ft| in the rate dynamic dFt=|Ft|βσtdWt, which naturally allows interest rates to across zero boundary. We focus on introducing FB-SABR into LMM to handle volatility smile under negative rates. This new model, FB-SABR-LMM, can be used to price interest rate instruments with negative strikes as well as to recover implied volatility surface.
1.
Introduction
There have been extensive studies and applications of Toeplitz and quasi-Toeplitz matrices recently. Toeplitz or quasi-Toeplitz matrices are adopted as a core tool in the quantum magnetic field [1], generation of random bits [2], quantum key distribution [3,4,5], the evaluation of the short-time rate of change in the trend of CO2 data [6], the deconvolution of hemodynamic responses [7] and the scattering and radiation on thin wire models [8]. Some studies have utilized Toeplitz or quasi-Toeplitz matrices to solve the ordinary and partial differential equations [9,10], also applying them to solve the fractional differential equations [11,12,13,14,15,16].
A large number of linear systems with Toeplitz coefficient matrices need to be solved. Recently, Liu et al. developed fast solvers for Toeplitz linear systems [17,18,19]. The inversion of the Toeplitz matrix is represented as a combination of circulant and skew-circulant matrices in [20,21] so that the solution can be gained directly by using the fast Fourier transform (FFT) and the inverse FFT (IFFT). Here, we turn to express the Toeplitz inversion by using the sum products of the skew-imaginary circulant [22] and skew-circulant matrices, where the skew-imaginary circulant matrix is an ω-circulant matrix with ω=−i, i=√−1.
Regarding the design of fast algorithms for a quasi-Toeplitz linear system, the authors of [23] presented new efficient algorithms to solve the CUPL-Toeplitz linear system [24,25,26] by first splitting the CUPL-Toeplitz matrix into a Toeplitz matrix and a low-rank matrix. In [27], Zhang et al. studied order-reduction algorithms to further reduce the computation complexity. The tridiagonal quasi-Toeplitz linear system is solved in [28].
We are concerned with a class of quasi-symmetric Toeplitz linear systems. The authors of [18] showed the trigonometric transformation splitting method to solve the real symmetric Toeplitz linear system. Different from the iterative method, we adopt the direct method based on the symmetric Toeplitz inversion representation, which is simplified due to the symmetry. We also show the numerical stability of the splitting symmetric Toeplitz inversion inspired by previous studies [26,29,30].
In this paper, we study an n×n real symmetric Toeplitz matrix with perturbations in the first and last columns P=(pj,k)nj,k=1∈Rn×n:
Obviously,
where α=[0,ς1,0,…,0]T, e1=[1,0,…,0]T is the first unit vector, β=[0,…,0,ς2,0]T, en=[0,…,0,1]T is the last unit vector and A=(t|j−k|)nj,k=1 is a nonsingular symmetric Toeplitz matrix.
An outline of this paper is as follows. Section 2 solves a sequence of linear systems with the same symmetric Toeplitz coefficient matrix. Section 3 presents the solvers for the quasi-symmetric Toeplitz linear system. A discussion of the quasi-symmetric Toeplitz matrix-vector multiplication is presented in Section 4. In Section 5, the stability analysis of the splitting inverse of the symmetric Toeplitz matrix is shown. Different numerical examples are given in Section 6. In Section 7, images are encrypted and decrypted by using the proposed quasi-symmetric Toeplitz matrix. Finally, we express our conclusions in Section 8.
2.
Solving symmetric Toeplitz linear systems with the same coefficient matrix
The starting point of the algorithms derived in this paper is the following inversion formula of Toeplitz matrices:
Lemma 1. [31,p. 738] Let A=(tj−k)nj,k=1∈Rn×n be a Toeplitz matrix. If the vectors x=[x1,x2,…,xn]T, x1≠0 and y=[y1,y2,…,yn])T are the solutions of the linear systems
Then A is invertible and
where SI1 and SI2 are skew-imaginary circulant matrices [22] holding the first columns as x=[x1,x2,…,xn]T and ˜y=[iyn,y1,y2,…,yn−1]T respectively; S1 and S2 are skew-circulant matrices with the first columns ˆy=[−yn,y1,y2,…,yn−1]T and x=[x1,x2,…,xn]T respectively.
Note that we are concerned with a symmetric Toeplitz matrix A; then, the special structure means that the solutions x and y in Eq (2.1) satisfy y=Jx, where the matrix J is an anti-identity matrix of order n.
If Ax=e1 has the solution x=[x1,x2,…,xn]T and x1≠0, then the symmetric Toeplitz matrix A is invertible and Eq (2.2) can be rewritten as
where SI and S have the same first column x=[x1,x2,…,xn]T and the symbol S∗I denotes the conjugate transpose of SI.
Performing the diagonalization scheme on the skew-imaginary circulant matrix, that is, SI=Ω∗nF∗nΛSIFnΩn, we can obtain
where Fn=(Fj,k)nj,k=1, Fj,k=1√ne2πi(j−1)(k−1)n, 1≤j,k≤n, Ωn=diag(1,e−3iπ2n,…,e−3i(n−1)π2n) and ΛSI is a diagonal matrix containing the eigenvalues of SI.
Equation (2.4) shows a new decomposition of the symmetric Toeplitz inversion. By taking full account of the structural characteristics of the symmetric matrix, we solve only one system Ax=e1 instead of two linear systems.
In the case of solving a sequence of linear systems with the same coefficient matrix, it is effective to solve Ax=e1 first and then use the new decomposition of the inverse of the symmetric Toeplitz matrix for calculation. Therefore, Algorithm 1 is proposed for the computation of x and the eigenvalues of SI. By applying Eq (2.4), an order-reduction algorithm [27] and FFT and IFFT operations, Algorithm 2 realizes the product of A−1 and v in the real number fields.
In the proposed algorithms, the diagonal matrix can be represented by a vector containing the diagonal entries; then, the multiplication of the diagonal matrix and the vector is implemented by using a dot product, thus reducing the storage and computational complexity.
To solve a sequence of linear systems with a constant symmetric Toeplitz coefficient matrix, Algorithm 1 only needs to be computed once. The first step in Algorithm 1 is to solve the symmetric Toeplitz linear system Ax=e1. Any symmetric Toeplitz linear solver can be used, such as the generalized minimal residual (GMRES) method, simplified quasi-minimal residual method, conjugate gradient (CG) method, etc. Since A is set as a symmetric positive definite matrix in our numerical experiments in this paper, we choose a the preconditioned CG (PCG) method with the Strang circulant preconditioner [32] to solve it. The workload of Algorithm 1 is considered to be O(nlog2n).
One FFT or IFFT needs 5nlog2n+O(n) real arithmetic operations [33,p. 75], and one run of Algorithm 1 in [27] needs 15n2log2n+O(n). Algorithm 2 mainly consists of two FFTs, one IFFT and two runs of Algorithm 1 in [27]. In the first step of Algorithm 2, it can save two FFTs with the length n2 when calculating STv and Sv simultaneously. Finally, we regard the workload of Algorithm 2 as 25nlog2n+O(n). The application of the order-reduction algorithm reduces the entire computational complexity.
A sequence of Toeplitz linear systems with the same coefficient matrix is solved in [20,21,34]. The method of using the splitting Toeplitz matrix inversion greatly saves the computational time. This reminds us that in a mathematical or engineering problem, we may be faced with thousands of linear systems with the same symmetric Toeplitz matrix. By applying Algorithm 2, it will be more efficient to solve these symmetric Toeplitz linear systems.
3.
Quasi-symmetric Toeplitz linear solvers
In this section, we solve a real quasi-symmetric Toeplitz linear system
where a=[a1,a2,…,an]T is an unknown vector and b=[b1,b2,…,bn]T is known. The coefficient matrix has a decomposition shown in Eq (1.2). We substitute Eq (1.2) into Eq (3.1) and multiply both sides of the equation by A−1 from the left; given that In is an identity matrix, we have
Let A−1α=μ, A−1β=ν and A−1b=η, where μ=[μ1,μ2,…,μn]T, ν=[ν1,ν2,…,νn]T and η=[η1,η2,…,ηn]T. The solution of Eq (3.2) can be
Therefore, solving Pa=b is the same as calculating Eq (3.3). Based on the Sherman-Morrison-Woodbury (SMW) formula [35], (In+μeT1+νeTn)−1 can be represented as
where C=(cj,k)nj,k=1 and
According to Eqs (3.3)–(3.5), we have
To solve the linear system Pa=b, we must solve the symmetric Toeplitz systems Aμ=α, Aν=β and Aη=b at first. By using Algorithms 1 and 2 and Eqs (3.5) and (3.6), we obtain the following:
Similarly, if we multiply Eq (1.2) by A−1 from the right, we can get P=(In+αeT1A−1+βeTnA−1)A and substitute it into Eq (3.1); then,
Denote eT1A−1=ρT, eTnA−1=σT and Aa=ψ, where ρ=[ρ1,ρ2,…,ρn]T, σ=[σ1,σ2,…,σn]T and ψ=[ψ1,ψ2,…,ψn]T. Then, Eq (3.7) can be rewritten as
The SMW formula is applied to Eq (3.8); we can write
where D=(dj,k)nj,k=1 and
From Eqs (3.8)–(3.10), we can get
Since A is a symmetric Toeplitz matrix, if eT1A−1=ρT and eTnA−1=σT, then Aρ=e1 and Aσ=en. According to Eqs (3.10) and (3.11) and the proposed algorithms in Section 2, we propose another algorithm for solving Pa=b.
From the above analysis, it is quite evident that the main work of Algorithms 3 and 4 is solving three symmetric Toeplitz linear systems. Moreover, we can omit one calculation of Aρ=e1 in Algorithm 4.
A greater number of symmetric Toeplitz linear systems will need to be solved if there are more perturbations in the coefficient matrix of the quasi-symmetric Toeplitz linear system. It is therefore meaningful to decompose the inverse of the symmetric Toeplitz matrix, as it will save computational time, especially in the case of high-order systems.
4.
Fast algorithm for the product of the quasi-symmetric Toeplitz matrix and vector
In terms of quasi-symmetric Toeplitz matrix-vector multiplication, the symmetric Toeplitz matrix A can be seen as the sum of the circulant and skew-circulant matrices [36], that is,
where v=(v1,v2,…,vn) is the vector and the circulant matrix C and the skew-circulant matrix S are all symmetric.
The first columns of circulant and skew-circulant matrices need to be computed in the splitting step. Considering the symmetry of n-th order A, the first columns of C and S can be obtained by applying the first n2+1 (n is even) or n+12 (n is odd) elements instead of n elements, which can reduce the computation complexity.
Based on the diagonalization scheme of the circulant matrix, C has the spectral decomposition C=F∗nΔCFn, where Fn=(Fj,k)nj,k=1, Fj,k=1√ne2πi(j−1)(k−1)n, 1≤j,k≤n, and ΔC is a diagonal matrix containing the eigenvalues of C. In [27], an order-reduction algorithm for the multiplication of the real skew-circulant matrix and vector is proposed. So the product of the quasi-symmetric Toeplitz matrix and vector can be expressed as
By applying Eq (4.2), the order-reduction algorithm for real skew-circulant matrix-vector multiplication, the FFT and IFFT operations, we give Algorithm 5 for Pv in the real number field as follows.
Because the complexity of one FFT or IFFT is 5nlog2n+O(n) [33,p. 75], Algorithm 1 in [27] needs 15n2log2n+O(n) real arithmetic operations. The complexity of Algorithm 5 is 45n2log2n+O(n), and it consists of one order-reduction algorithm, two FFTs and one IFFT.
5.
Stability analysis
We find that the inverse factorization of the symmetric Toeplitz matrix is critical for the solution of quasi-symmetric Toeplitz linear equations. The following is the error analysis of Eq (2.3) in terms of the 1-norm, ∞-norm and 2-norm, respectively. Assume that ˆx=[ˆx1,ˆx2,…,ˆxn]T is the numerical solution of Ax=e1. If ˆx1≠0, we denote
as a perturbation of A−1, where the forms of ˆSI and ˆS are the same as those in Eq (2.3) and have corresponding perturbations.
Theorem 1. Let ϵ>0; if x1≠0 and ˆx1≠0, suppose that the relative error of 1x1 is ˆϵ=|1/x1−1/ˆx1||1/x1| and
we get
and
Proof. From the representation of A−1 and ˆA−1 and Eqs (2.3) and (5.1), we can get
On the one hand, we can get
According to the structural characteristics of SI and S and Eq (5.2), we note that
ˆϵ=|1/x1−1/ˆx1||1/x1| is the relative error; then,
Combining Eqs (5.6)–(5.8), we thus obtain
Similarly, on the other hand,
Based on Eqs (5.5), (5.9) and (5.10), we can write
By Ax=e1, it is proven that ‖x‖1≤‖A−1‖1, so
Theorem 2. Let ϵ>0; if x1≠0, ˆx1≠0 and
then
and
where ˆϵ=|1/x1−1/ˆx1||1/x1| is the relative error of 1x1.
Proof. Similar to Theorem 1, this proof is based on the same conditions:
and
Theorem 3. Under the assumptions and concepts of the previous two theorems, the upper bound of the 2-norm is said to be
and
Proof. As we all know, ‖A−1−ˆA−1‖22≤‖A−1−ˆA−1‖1⋅‖A−1−ˆA−1‖∞; from Eqs (5.3) and (5.12), we have
Recall that
From Eqs (5.14) and (5.16), we can get
We show the stability analysis of inverse factorization of the symmetric Toeplitz matrix in this section. The absolute and relative perturbation upper bounds are shown in Eqs (5.3) and (5.4), (5.12) and (5.13), (5.14) and (5.15), as far as Ax=e1 is solvable.
6.
Numerical simulations
In this section, we give some examples for the comparison of different algorithms. The first two examples present a comparison of different quasi-symmetric Toeplitz linear solvers. Examples 3 and 4 are devoted to the fast algorithm for the quasi-symmetric Toeplitz matrix-vector multiplication.
These experiments were done by using MATLAB (R2022a) on a laptop with the following specifications: 16 GB RAM, AMD Ryzen 7 5800H CPU 3.20 GHz. In the following tables, the calculation time is in seconds, "n" denotes the matrix order and "—" indicates that it is out of MATLAB's memory.
Example 1. An n×n quasi-symmetric Toeplitz linear system Pa=b is considered in this example. According to Eq (1.2), the first column of A is (ti)ni=1=1i, and ς1 and ς2 are random values in the range of (0,1). Assume that aexact=[1,1,...,1]T is the exact solution, so the vector b is b=Paexact.
A comparison of the error and time required to solve a quasi-symmetric Toeplitz linear system is presented in Table 1. The derived two algorithms for solving Pa=b are shown in the table as Algorithms 3 and 4. Based on Algorithm 3, AlgHuang Ⅰ replaces Steps 1 and 2 with Huang's algorithm [20,21] for solving three symmetric Toeplitz systems. Similarly, AlgHuang Ⅱ was executed based on Algorithm 4. The back-slash method means solving Pa=b directly by using the back-slash operator in MATLAB. "Error" was set to be ‖a−aexactaexact‖∞, and the stopping criterion for those algorithms, besides Back-slash, was set to be 1×10−7.
Algorithms 3 and 4 have significate superiority over the other methods. They can solve high-order quasi-symmetric Toeplitz linear systems. However, Back-slash cannot work when the matrix order is above 214. The proposed Algorithms 3 and 4 have the shortest computational time. They perform better than AlgHuang Ⅰ and AlgHuang Ⅱ in high-order linear systems due to the application of the order-reduction algorithm.
Example 2. Consider another quasi-symmetric Toeplitz linear system Pa=b, the first column of A and that ς1 and ς2 in Eq (1.2) are generated from an open interval (0,1). The sum of the elements in the first column was added to the diagonal entries of A to keep A as a diagonally dominant matrix. The exact solution of the system was set to be aexact=[1,1,...,1]T.
Table 2 shows a comparison of different methods for solving Pa=b for Example 2. AlgPGMRES refers to solving the linear system by using the GMRES method with the preconditioner. Since P is a nonsymmetric matrix, the GMRES method can be utilized to solve Pa=b. In order to accelerate the convergence rate, the Strang circulant preconditioner [32] of the symmetric Toeplitz matrix A was established.
According to theoretical analysis, the complexity of Algorithm 4 is lower than that of Algorithm 3. The results show that Algorithm 3 takes more time than Algorithm 4, which is consistent with the theoretical analysis. AlgPGMRES performs better than the other methods. However, compared with the algorithm for solving symmetric systems, the convergence analysis of the GMRES algorithm is very difficult, and there is no clear conclusion at present.
Example 3. Consider the multiplication of Pv. The vector v is Gaussian distributed. The quasi-symmetric Toeplitz matrix P is decomposed as Eq (1.2), where the first column of A is (ti)ni=1=1i and ς1 and ς2 are random values in the range (0,1).
In Table 3, Pv-direct denotes calculation of the quasi-symmetric Toeplitz matrix-vector multiplication via MATLAB. Pv-splitting refers to splitting P according to Eq (4.1) first, and then utilizing the diagonalization scheme of the circulant matrix and skew-circulant matrix for fast calculation. Algorithm 5 is the proposed quasi-symmetric Toeplitz matrix-vector multiplication. Obviously, Algorithm 5 consumed the least amount of time.
Example 4. Consider the multiplication of Pv, the first column of A, ς1 and ς2 in Eq (1.2), and that the vector v are random values in the range (0,1). The sum of the elements in the first column was added to the diagonal entries of A.
Table 4 shows another example for the quasi-symmetric Toeplitz matrix-vector multiplication. As the matrix order increases, the efficiency of Algorithm 5 becomes increases. Our proposed algorithm is suitable for high-order matrix-vector multiplication. However, the Pv-direct method not only takes the longest time, but it also cannot work when the matrix order is above 214.
7.
Applications
In the past decades, image encryption and decryption have been widely researched in the area of information security. The results show that the proposed algorithms can be used to encrypt and decrypt images.
Example 1. Based on Eq (1.2), we consider a quasi-symmetric Toeplitz matrix P, where the entries in the first column of A and ς1 and ς2 are random values in the range (0,1). To keep P as a diagonally dominant matrix, we added a parameter to the diagonal entries of P. Images were encrypted and decrypted by left-multiplying by P2 and P−2, respectively.
Figures 1–3 present the effects of image encryption and decryption. The famous figure "Lenna" is taken as an example. Let the original image matrix be X=[x1,x2,…,x256]; the encrypted image matrix can be obtained by matrix-vector multiplication via Algorithm 5, that is, Y=[y1,y2,…,y256]=P(P[x1,x2,…,x256]). The decrypted image matrix can be computed by ˆX=[ˆx1,ˆx2,…,ˆx256]=P−1(P−1[y1,y2,…,y256]). Algorithm 4 was performed for image decryption because of its lower complexity than Algorithm 3.
In the process of image encryption and decryption, it is necessary to do multiple matrix-vector multiplications with the same quasi-symmetric Toeplitz matrix and solve linear systems with the same coefficient matrix. Some calculations can be done only once, like Steps 1 and 2 of Algorithm 5 in image encryption, as well as Steps 1 and 2 of Algorithm 4 in image decryption. So, the computational time will be saved.
It is obvious that our proposed algorithms can realize efficient encryption and decryption for different pixel-sized images.
8.
Conclusions
Algorithms for solving a class of real quasi-symmetric Toeplitz linear systems are shown in this paper. We have proposed methods for solving a sequence of linear systems with the constant symmetric Toeplitz matrix based on the decomposition of Toeplitz matrix inversion. By splitting the coefficient matrix into a symmetric Toeplitz matrix plus two low-rank matrices and combining it with the SMW formula, two fast algorithms with O(nlog2n) complexity have been given to solve the real quasi-symmetric Toeplitz linear system. Quasi-symmetric Toeplitz matrix-vector multiplication in the real number field has been presented. Structural perturbation analysis of the inverse factorization of symmetric Toeplitz was also analyzed. Numerical simulations and applications have shown that the proposed algorithms are accurate and efficient.
Acknowledgements
The research was supported by the National Natural Science Foundation of China (Grant No. 12101284) and Natural Science Foundation of Shandong Province (Grant No. ZR2020MA051).
Conflict of interest
The authors declare that there is no conflict of interest.









 DownLoad:
DownLoad: